What’s an Autonomous SOC?
Modernizing Security Operations (SecOps) is essential to combat the growing volume and sophistication of threats. Autonomic and autonomous security operations are terms increasingly used to describe cybersecurity solutions that enable this modernization.

Autonomous vs Autonomic SOCs, Explained
While both terms relate to automation and self-governance, “autonomic” and “autonomous” have distinct connotations within a cybersecurity context.
Autonomic systems
are self-managing and can adapt to changing conditions, but they still operate within predefined boundaries and rules.
Autonomous systems
are self-governing and can make independent decisions without human intervention.
Autonomic systems focus on maintaining a stable and secure state by adjusting their behavior based on internal and external feedback.
Autonomous systems have a greater degree of freedom and can learn and evolve based on their experiences.
Autonomic Security Operations combines philosophies, practices, and tools to improve an organization’s ability to withstand security attacks through an adaptive, agile, and highly automated approach to threat management.
Autonomous Security Operations would imply a higher level of self-governance, where security systems could independently identify, analyze, and neutralize threats without human input.
With autonomic security operations, the goal is to achieve a 10X improvement across people, processes, technologies, and organizational influence.
Autonomous security operations requires advanced Gen AI capabilities, which are still emerging in the cybersecurity domain.
Why SOCs Need An ASOC Solution
Alert Fatigue
SOC teams are bombarded with an overwhelming number of alerts, many of which are false positives.
Siloed Functions
Disparate tools and isolated teams lead to communication gaps and fragmented threat responses.
Resource Shortages
Budget and staffing limitations restrict the SOC’s ability to effectively monitor and respond to threats.
Relentless Threat Landscape
The increasing sophistication and volume of cyberattacks demand quicker and more accurate detection and response.
Legacy Automation Limitations
Legacy SOAR solutions often require significant investments on playbook development and maintenance, without delivering the expected return on investment.
High Operational Costs
Maintaining traditional SOC infrastructure and monitoring tools is increasingly expensive.
Struggle with Visibility
Even top-tier SOCs can miss critical alerts due to the sheer volume and diversity of data sources.
Key Components of an Autonomous SOC Solution
An autonomous SOC incorporates several critical elements to continuously monitor, investigate, and respond to threats with minimal human intervention. Below are the core elements of Morpheus that make up this modern approach:
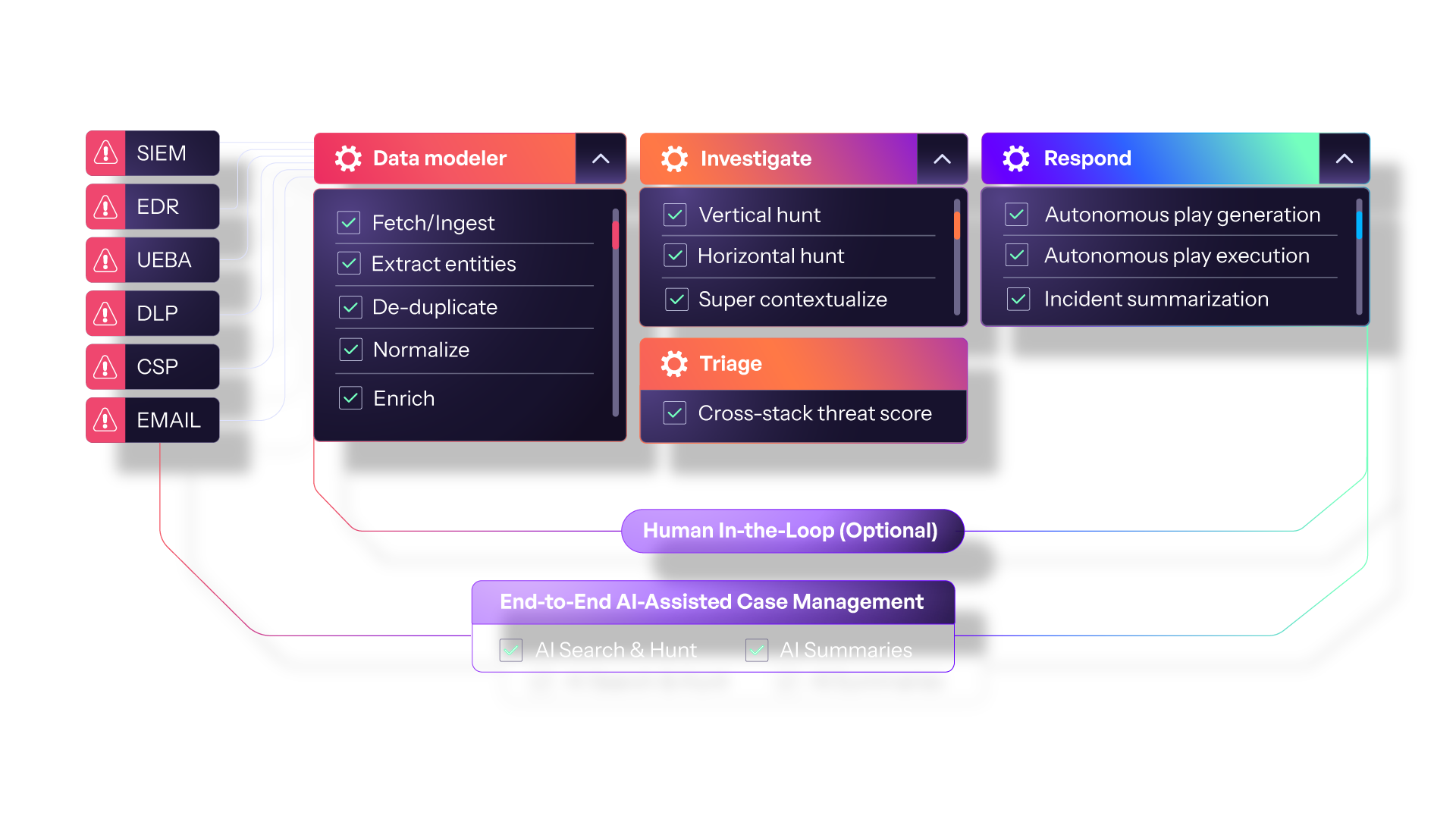
Morpheus ASOC provides an AI-driven, end-to-end security operations workflow that executes autonomous responses with optional human oversight.
Data Ingestion and Modeling
Diverse Data Sources
Collect security events and alerts from a broad range of tools, such as SIEM, EDR, and email security solutions.
Entity Extraction and Deduplication
Identify key objects (e.g., IP addresses, file hashes) while consolidating duplicate data.
Normalization and Enrichment
Convert disparate data into a consistent format and augment it with external context (e.g., threat intelligence, asset details).
Investigation and Triage
Vertical and Horizontal Hunts
Explore incidents in depth (vertical) and hunt for related threats across multiple systems (horizontal).
Contextualization
Automatically link relevant intelligence—such as vulnerability data or known adversary profiles—to each investigation.
Cross-Stack Threat Scoring
Aggregate risk signals from all integrated systems to produce a unified severity or priority rating, ensuring critical threats get immediate attention.
Automated Response
Playbook Generation and Execution
Automatically build and execute incident response workflows (e.g., isolating a host, blocking an IP).
Incident Summaries
Generate concise reports on the incident’s scope, actions taken, and outcomes.
Human-in-the-Loop (Optional)
Analyst Oversight
While automation covers routine tasks, analysts can intervene for high-level decision-making or complex scenarios.
AI-Assisted Case Management
AI-Driven Search and Hunt
Identify patterns, anomalies, and potential threats across historical and real-time data.
Summarization
Transform large volumes of raw data into actionable insights.
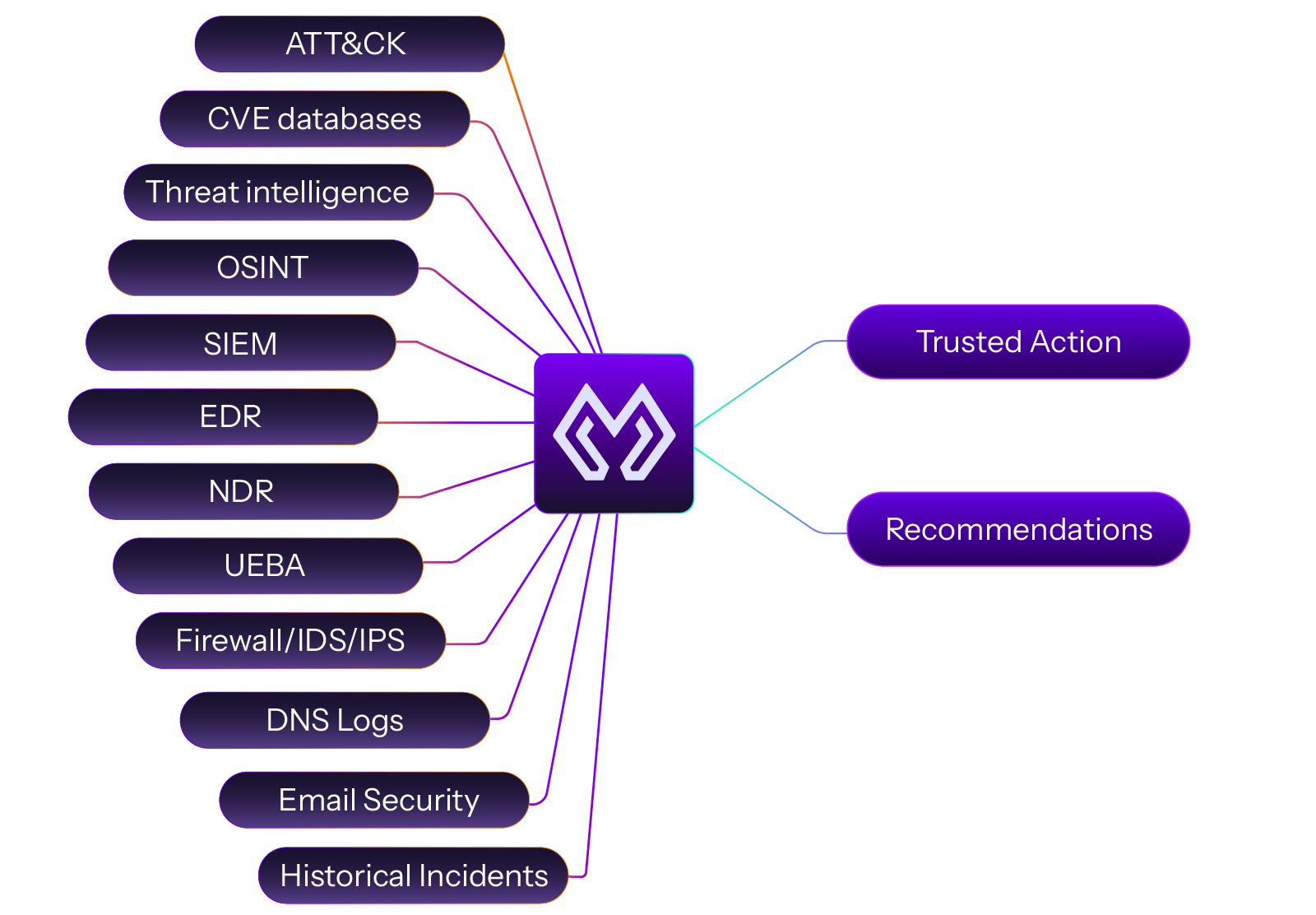
Extensive Integrations
Broad Tool Compatibility Connect seamlessly to hundreds of security tools and data sources, ensuring a comprehensive view of the organization’s threat landscape.
Challenges and Barriers to Autonomous SOC Adoption
From trust deficits to opaque “black box” solutions, organizations face several challenges.
- Trust Issues
Many security teams remain skeptical of AI solutions due to concerns over reliability and the opaque nature of algorithmic decision-making. - Limited Customization & Black Box AI
Vendors often restrict the fine-tuning of models, leaving organizations with a one-size-fits-all approach that may not fit their unique security posture. - Analyst Involvement
Human oversight remains crucial for validating findings, managing escalations, and adapting workflows to complex, evolving threats. - Accuracy & Efficacy Concerns
Questions linger about whether current models can effectively balance false positives and negatives without compromising critical threat detection.

Industry analysts and practitioners warn that true “set-and-forget” security remains unrealistic. Forrester’s Allie Mellen famously branded the concept a “pipe dream” in 2022, citing fragmented data and incompatible tools as major obstacles.
SentinelOne introduced a five-stage Autonomous SOC Maturity Model in 2024, reframing the Autonomous SOC not as a replacement for human analysts but as a “symbiotic relationship” where AI handles repetitive tasks, freeing analysts for strategic work.
Industry analysts now recognize Autonomous SOCs as a viable—though evolving—paradigm. Current consensus holds that:
Human-Machine Collaboration Is Essential
Autonomous SOCs thrive when AI handles repetitive tasks, enabling analysts to focus on exception handling and strategic defense.
Continuous Adaptation Is Critical
Systems must learn from feedback loops, incorporating new threat intelligence and adversarial tactics.
Ethical Governance Matters
Organizations must audit AI systems for bias, transparency, and compliance to avoid unintended consequences.

The D3 Approach
Morpheus: Built for Privacy, Tuned for Precision
✅ Private
✅ D3-hosted
✅ Stateless
✅ Tenant Scoped
✅ No Logging
✅ No Storage
✅ No Training
✅ No Internet
Trust & Customization
Unlike many AI platforms, Morpheus’s fine-tuned models are exclusively for D3’s use—ensuring you’re not sharing or diluting your data across third-party environments.
Enhanced Accuracy
With zero data retention and in-memory processing only, Morpheus minimizes data exposure while delivering precise, reliable threat detection.
Analyst Empowerment
By integrating AI with human expertise, Morpheus streamlines validations and escalations, ensuring that your analysts remain at the helm of security operations.
Learn More About Morpheus
Check out these resources to answer your questions about our other cutting-edge capabilities.
-
Morpheus: AI-Driven Autonomous Investigation, Triage, and Response
Uncover how Morpheus’s AI-driven investigation capabilities transform alert handling from hours to seconds while keeping humans strategically positioned.

-
The CISO’s Guide to Autonomous SecOps
Explore how Morpheus powers autonomous SecOps with complete alert coverage and lightning-fast triage—no stack replacement required. Real case studies included.

-
The State of the Autonomous SOC: Drivers, Risks, and Opportunities
Explore how autonomous security operations and AI-driven response are reshaping enterprise defense.

Ready to see Morpheus?
Morpheus is ready to transform your SOC—intelligent, AI-driven security that adapts to you. See it in action. 🚀
