Threat Hunting
Investigate and Hunt for Hard-to-Find Threats
Smart SOAR makes it easy to locate threats in your environment, wherever they’re hiding. Using signature and behavior-based methods, Smart SOAR’s cyber threat hunting playbooks enable you to uncover connections, identify dangers, and proactively search for ongoing incidents.
Take a Proactive Stance Against Cyberattacks
Follow the Links Between IOCs
Smart SOAR extracts indicators of compromise (IOCs) from incoming alerts and uses them to run searches across your entire environment. Find IOCs across other events, logs, and endpoints, while expanding your understanding of the incident by incorporating linked IOCs into the search.
Keep an Eye on Potential Threats
When a sign of a potential attack is detected, you can monitor the behaviors that would represent further links in that kill chain. Surveillance allows you to keep a constant eye on the most important IOCs and TTPs, knowing that you’ll be alerted immediately when they’re involved in an incident.
Visualize Trends with the MITRE ATT&CK Matrix
Track and visualize the occurrence of each ATT&CK technique in your environment with Smart SOAR’s MITRE ATT&CK Monitor dashboard. You’ll know at a glance what techniques your adversaries are using against you and where to focus your resources.
Orchestrate Advanced Threat Hunting Playbooks
Orchestrate threat hunting workflows with Smart SOAR’s automation-powered Tier 3 playbooks. Contextualize security events using integrations with email, identity, endpoint, and network tools. Identify connections between events and widen the scope to find related IOCs across your organization.
“Not only are we able to reduce the overhead associated with manual labor, but… additionally, the automation aspect allows us to branch out to other areas of the attack surface, further enhancing our ability to prevent security breaches.”
The Smart Soar Approach
Automate Cyber Threat Hunting
Security teams don’t have the time for slow and manual cyber threat hunting tools, which allow dangerous threats to go undetected. The solution is automation-powered threat hunting.

Integrate Your Tools
With unlimited integrations, Smart SOAR can orchestrate threat hunting that covers your entire environment from one interface.

Easily Operationalize Intelligence
Automatically parse reports from integrated threat intelligence sources and search for their IOCs to ensure you’re always up to date with potential risks.
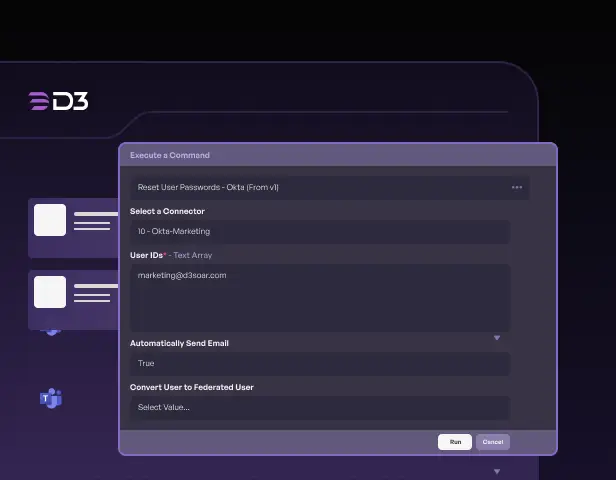
Manage Investigations
Make it easy to schedule automated threat hunts, minimize manual steps, and review the results, using Smart SOAR’s playbooks and investigation management features.
Resources for Cyber Threat Hunters
To learn more about why Smart SOAR stands alone among cybersecurity threat hunting tools, check out these resources.
-
A Comprehensive Guide to Smart SOAR
Learn how Smart SOAR outperforms conventional SOAR tools in every aspect of threat detection, analysis, and incident response.

-
How High Wire Networks Eliminated 99% of Alert Noise and Increased Capacity 3x Without Adding Headcount
Serving 25k+ customers through a global network of channel partners, Master MSSP High Wire Networks used Smart SOAR to cut alert noise by 99% and 3x client capacity without adding headcount.
-
Take Action on Threat Intelligence with Smart SOAR
Discover how Smart SOAR operationalizes cyber threat intelligence, enhancing your security posture with streamlined, automated workflows.