Here’s the thing. I dislike it when interviewers ask basic questions. It makes for a boring interview. And as the host of the Let’s SOC About It podcast, I try to avoid “starting from the very beginning” and asking the most obvious questions. So usually, when I get the opportunity to interview someone like Tony UcedaVelez– who comes in with a wealth of knowledge on MSSP strategy, Threat Modelling, and security methodology– I try to ask interesting, thought-provoking questions.
HOWEVER, as I sat down to prepare for my interview with Tony– the creator of the PASTA Threat Modelling Methodology– I had to ask myself, what is threat modelling? Is it the same as “threat hunting”? Is it “threat response”? Is it “threat detection”?

To get clarification, I asked our engineering team, who all had different definitions of threat modelling. I was even more confused.
So, to find out, I decided to commit the faux pas and ask The Godfather of Threat Modelling himself.
And to my delight and surprise, he said “a lot of people are asking the same exact question”.
What Is Threat Modelling?
“In simple terms, the definition of threat modelling is building a model of threats,” says Tony UcedaVelez.
The goal of a threat model is to uncover threats and prepare to handle them.
To build a threat model, in part, is to build a comprehensive list of threats and all its details. It goes beyond MITRE threats and tactics. It provides contextualized information about the threat that anyone, not just security-focused stakeholders, can understand.
What Is the Difference Between Threat Modelling and Threat Detection / Response / Hunting?
Threat detection, response, and hunting are operational tactics to uncover threats. It involves harvesting intel and parsing through hacker forums.
On the other hand, threat modelling is more strategic and looks at what could undermine operations. Threat modelling encompasses more contextualized data to help you make more informed decisions. And, threat modelling falls under a higher umbrella category than threat detection, as threat detection can be part of threat modelling.
How Do You Create a Threat Model?
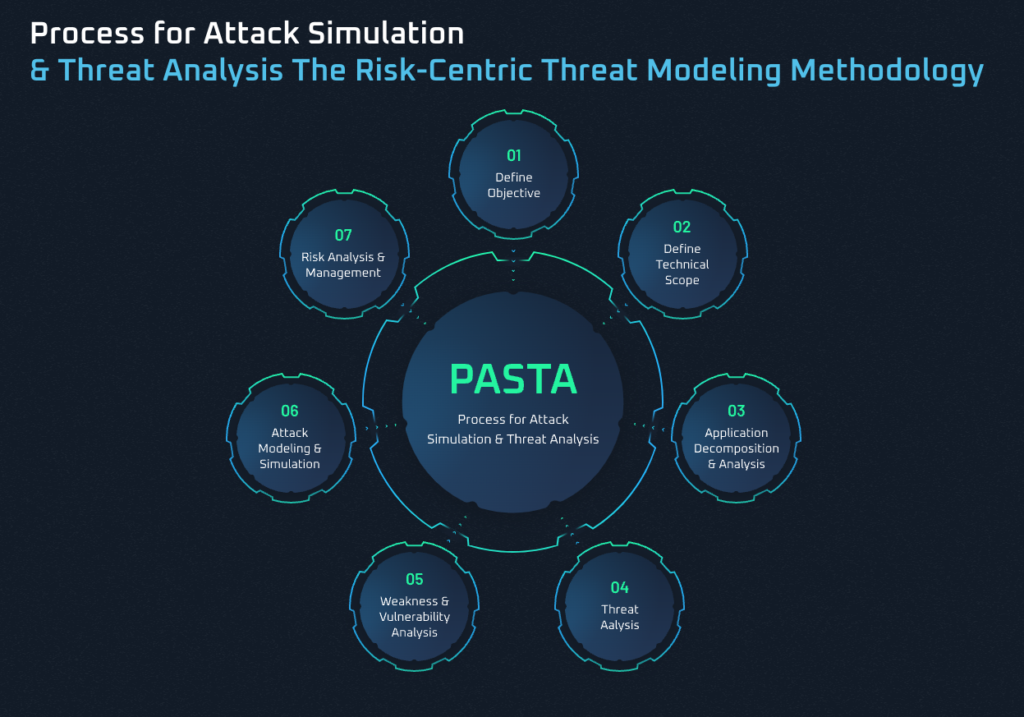
Tony recommends the PASTA (Process for Attack Simulation & Threat Analysis) threat methodology. It’s a 7-stage process that contextualizes threats.
- Define Objectives: Identify the business objectives, taking requirements into account
- Define the Attack Surface: Enumerate attack surface components across infrastructure, systems, and data layers
- Application Decomposition: Identify authentication model, protocols, and trust boundaries
- Threat Analysis: Research and correlate threat advisories and intel
- Vulnerability & Weakness Analysis: Correlate network, cloud, and supply chain vulnerabilities with an attack tree
- Attack Modelling: Build an attack library and map to defined weaknesses and vulnerabilities, define attack probability, correlate data
- Risk & Impact Analysis: Identify relevant threat trends, estimated impacts, recommendations, and more.
How Do You Offer Threat Modelling as a Service?
Tony and the VerSprite Security team offer Threat Modelling as a Service to their customers. The end product is a combo of graphs and text-based reports that breaks down residual risks, potential impact, distribution of threats, and more– all wrapped up into a pretty dashboard.
Tony and his team work with their customers to understand their environment, enumerate their tech stack, research threats, build attack trees and libraries, and provide detailed recommendations and analysis of the potential impact of an attack.
Tony’s Advice on How To Start Threat Modelling
To start engaging in threat modelling, Tony recommends referencing the free Fork Community edition of the PASTA threat model. Within the GitHub Fork Community page, you’ll find VerSprite’s free list of industry-specific threat libraries.
These free tools help you map vulnerabilities to industry-specific threats– ranging from disrupting energy production at a power plant to gaining access to unauthorized areas in hospitals.
And if you want more information about Threat Modelling, I’d highly recommend listening to the full podcast episode:
How Do VerSprite & D3 Go Hand-in-Hand?
VerSprite Security is a loyal D3 customer that uses D3’s automation to trigger events, correlate data, and respond to threats more accurately.
VerSprite continues to choose D3 as their automation partner for its scalability because D3 is architecturally built to scale. This means we offer our customers a place to automate security actions with full flexibility and customization.
Hear what Tony has to say about D3:




