Morpheus automates Tier 1 and Tier 2 SOC work across your Microsoft stack and third-party tools. Whether you use Sentinel, Defender, or Entra, it sits above them, investigating alerts and closing noise or escalating real threats with full context. Your team keeps control. The platform handles the volume.
Why Traditional MSSP Economics Are Breaking
Most MSSPs operate inside Microsoft daily. Sentinel manages incidents. Defender covers endpoints, email, and SaaS. Entra ID handles identity. Each new tenant adds their own mix—CrowdStrike, Fortinet, Palo Alto, Okta, AWS—which generates more alerts, more portals, and more Tier 1/2 work.
Traditional MSSP economics force a choice: scale and sacrifice service quality, or maintain quality and cap growth. As detailed in our previous blog, the industry is consolidating around this reality—forecasts show the top 200 MSSPs shrinking to about 120 by 2028 as mid-tier players get acquired and regional firms merge. The survivors will be those that scale efficiently without proportional headcount increases.
The Autonomous Layer Above Your Microsoft Stack
Morpheus connects to your existing tools—Sentinel, Defender, Entra, and your third-party stack. It:
- Ingests alerts from all sources into one normalized view
- Investigates automatically by gathering host details, identity activity, email traces, and network data
- Makes clear decisions by either closing noise with written explanations or escalating real incidents with evidence, narrative, and recommended actions
- Maintains tenant boundaries while correlating patterns where useful
Your analysts receive ready-to-act incidents instead of raw alerts. Microsoft investments stay intact. Your workflows stay yours.
Core Architecture: The Unified Autonomous Stack
Morpheus follows a structured as a three-layered stack that combines traditional automation with advanced AI reasoning, which enables it to act effectively on your behalf without becoming a black box. Each layer has a defined role you can see and control.
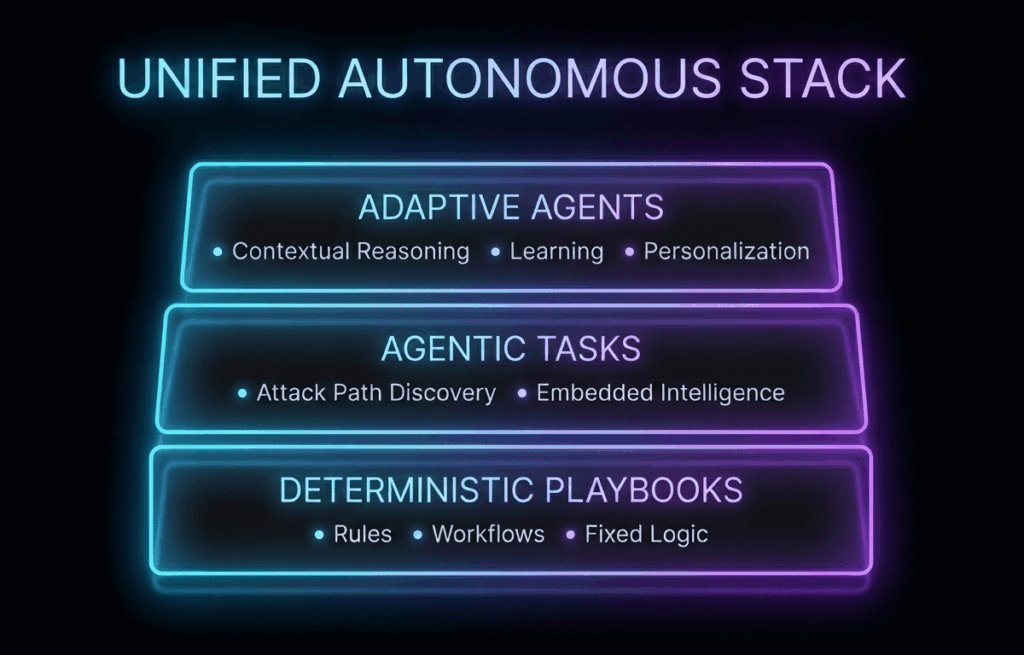
Deterministic Playbooks: Clear workflows around Sentinel, Defender, Entra, and tickets
Operating as structured playbooks, this is the base layer consisting of rule-based workflows, fixed logic, and standard procedures. It provides the necessary structure for incident response.
You decide which Sentinel incidents or Defender alerts trigger a workflow, which data sources to query, and what the start and end of that flow look like.
Example: A Microsoft phishing alert in Sentinel triggers a path where Morpheus pulls details from Defender for Office, checks Entra sign-ins for the affected user, looks for similar emails across the tenant, updates the case, and writes the outcome to your ticketing system.
These workflows keep control in your hands. You decide which actions run automatically (gathering data, generating incident and attack summaries) and which require human approval (isolating hosts, locking accounts). You also decide how this differs by tenant and service tier. Morpheus expresses your existing methods, not its own.
Agentic Tasks: An AI investigator inside each workflow
Inside those deterministic workflows sits a dedicated agentic AI investigator that can react and respond dynamically to live alerts and real-time data. It knows how to ask the next right question. Once the workflow collects initial details, this investigator examines context and decides how to dig deeper, launching new searches (based on a proprietary D3 framework) autonomously, and dynamically react to unseen data, even for unseen alerts or zero-day threats not covered by standard playbooks.
Essentially, they are the “reasoning brain” within playbooks that learn what to do next on live data, rather than following a fixed flowchart, helping the system react to unknowns and evolve with the threat landscape.
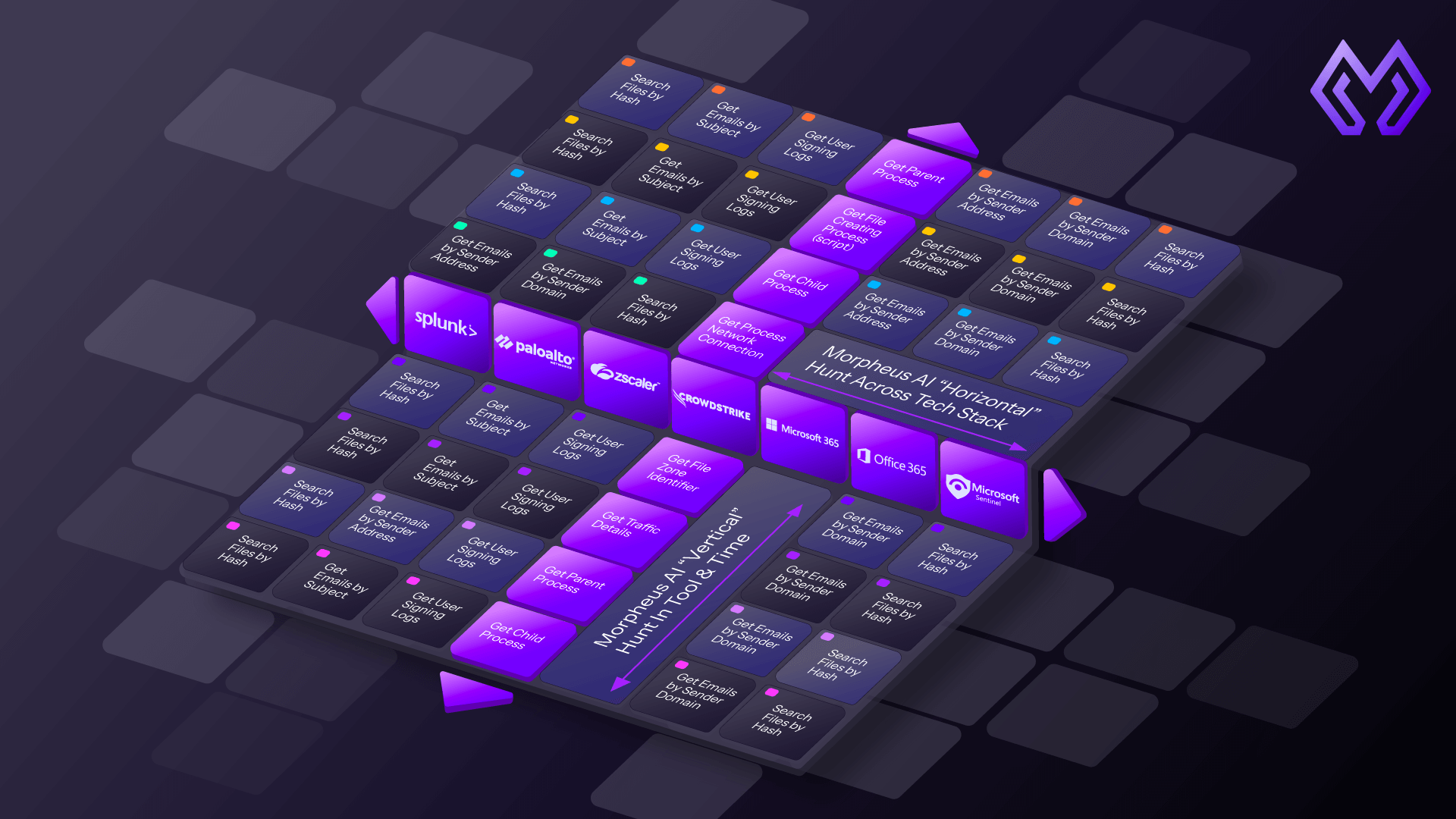
For a risky sign-in, it might pull more Entra sign-in history, examine risk levels and conditional access decisions, inspect Defender activity on the device, and query other XDR tools you use for that tenant. For possible phishing, it might trace the message across inboxes, examine URLs and attachments, look for process activity on endpoints, and check for related identity events. The AI investigator calls the right tools through Morpheus, gathers what it needs, and builds a narrative about what happened.
Layer 3: An adaptive agent across tenants and services
The top layer looks across everything flowing through the platform. It sees which alerts repeat across tenants, which patterns lead to real incidents, how your analysts respond to recommendations, and which steps happen repeatedly with no value added by a human. This layer makes Morpheus learn your business.
Over time, the agent suggests changes. It might surface a Microsoft alert type that never results in real incidents for certain tenants and propose a lighter path (auto-closure with clear record). It might show that identity-driven incidents tied to Entra and Defender have higher likelihood of being real and should receive higher priority and more aggressive playbooks. It might recommend turning repeated manual steps into fully automatic ones, with reasoning and audit logs to support that choice.
This layer turns data from thousands of investigations into concrete tuning ideas that protect margin. You decide what to adopt. Morpheus brings the patterns into view and makes them actionable.
The Economic Shift: SaaS Margins in a Services Business
- Scale without headcount: Onboard new tenants by connecting their Microsoft environment and key tools, not by hiring more analysts. As we covered in How MSSPs Turn Security Alerts Into Exponential Revenue, you’re decoupling revenue growth from cost growth entirely—a 50% increase in customers or a 200% surge in alert volume no longer forces you to double your SOC team.
- Protect margins: Reduce night and weekend staffing pressure while meeting strict SLAs. Around-the-clock coverage stops being a cost center and becomes table stakes delivered at a fraction of traditional expense.
- New service tiers: Package “autonomous SOC” for Microsoft-heavy customers. Morpheus lets you bundle remediation into service contracts. Monitoring contracts turn into MDR contracts. One-time incident response becomes recurring monthly revenue. You can tier offerings: basic customers get self-service remediation playbooks, premium customers get analyst-executed response, enterprise customers get proactive threat hunting plus response.
- Demonstrate Full transparency: Show clients detailed records of how alerts were handled, which evidence was checked, why certain actions were taken or skipped, complete forensic timelines with ATT&CK TTPs, and clear remediation recommendations. Your service quality becomes visible and defensible.
Morpheus absorbs the volume. Your team focuses on confirmed incidents, tuning, and client relationships. Growth becomes an asset, not a burden. Book a demo and watch Morpheus investigate live alerts from your Microsoft environment in real time.




