We’ve received a great response for our upcoming webinar with Elastic on November 16th and seats are filling up fast. Many of our customers use D3 Smart SOAR’s integration with Elastic, which is no surprise considering it is the most popular enterprise search engine. The webinar is a great opportunity for security leaders to learn how Smart SOAR’s integration with Elastic helps to detect, investigate and respond to threats at enterprise scale. The integration combines Elastic’s powerful detection, prevention, and response capabilities with Smart SOAR’s no-code automation and cross-stack orchestration capabilities to help security teams fight cybercrime more proactively, prevent attacks, and reduce analyst workload. Don’t miss this opportunity to glean insights on SecOps and IR automation from D3’s Security’s Stan Engelbrecht and Elastic’s James Spiteri in the Q&A session.
How Security Teams Use Elastic and D3 Security
The greatest value of the security operations center (SOC) is in its ability to quickly detect and respond to threats. With the powers of the Elastic Stack (also known as the ELK Stack, comprised of Elasticsearch, Logstash, and Kibana) and Smart SOAR combined, your SOC team can add continuous monitoring, alert triage, incident response, and threat-hunting capabilities.
Here are two use cases that highlight how our two products work together to reduce incident workload, improve response times, and make the right decisions faster.
Automated Alert Enrichment and Escalation
Ingest alerts from Elastic and automatically escalate real threats to incident status and assess their criticality through automated data enrichment and MITRE ATT&CK matrix correlation. Predefined Elastic queries can be used as the conditions to trigger an automation-powered playbook for fast and consistent triage and response.
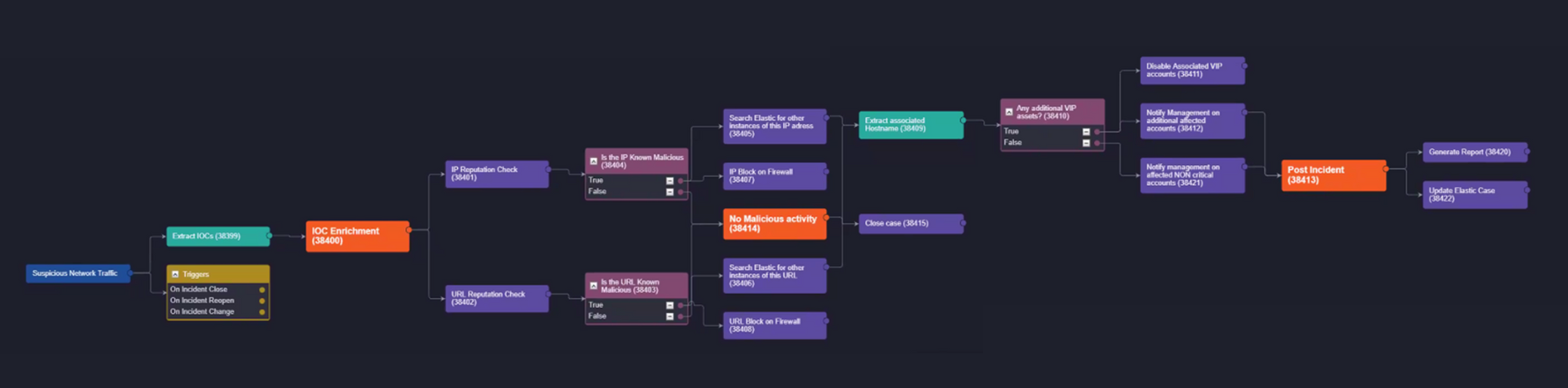
Let’s walk you step-by-step through a SOAR playbook that runs every time Elastic triggers a phishing email alert that’s ingested by D3 and escalated to an incident. The initial alert has a hostname, IP address, and URL.
- Smart SOAR extracts all the IOCs, and runs a reputation check on the IP, and the URL to check if they are malicious.
- If they’re non-malicious, then the playbook will just go ahead and close the incident. No further action is needed.
- If the IOCs are known to be malicious, two workflows get kicked off. One is an immediate update of the firewall to block the IP. The other is to start a query in Elastic for instances of the IP address within the ELK stack.
- It’s the same thing for the URL. The workflow starts a search for instances of the URL in Elastic and adds a URL block on the firewall.
- Because we’ve got the initial hostname, the playbook extracts the latest related hostnames that come back from these two queries. Now we have a set of hostnames that are associated with that known bad URL and IP that were part of the initial alert.
- The playbook then extracts the hostnames, and does a comparison. Is it a critical or VIP asset? If anything is found on these critical or VIP assets, disable those accounts immediately. We don’t want to take the chance.
- The playbook sends a notification to management of the critical and additional affected accounts.
- Post-incident, Smart SOAR generates a report and updates the case in Elastic.
Actionable Threat Intelligence
Most SOC teams get their threat intelligence from a variety of feeds. The challenging part is to make that threat intel actionable, whether it is IP addresses, possible bad domains, or file hashes. Those are all things that can be queried back into Elastic, to find instances of the IOCS, what users are affected by them, and then to take appropriate action. If you’re having to coordinate threat intelligence lookups, this can be scheduled through a playbook that ingests the threat intelligence and automates the running of the queries for those IOCs within Elastic.
Join our Webinar with Elastic on Nov 16th at 10AM PST
We’re excited to have you join us next week for our joint webinar with Elastic. The webinar, hosted by D3’s Stan Engelbrecht and Elastic’s James Spiteri will expand on the ideas presented in this blog and showcase some of the powerful ways to use Elastic and Smart SOAR to streamline your SecOps workflows.
James Spiteri works as a Product Marketing Director for Elastic and focuses on security. He developed specialized SIEM platforms for security operations centers (SOCs) across a range of different industries and sectors before he joined Elastic. James is also the creator of whichphish.com, eqlplayground.io, and log4shell.threatsearch.io.
Stan Engelbrecht, CISSP, is the director of cybersecurity practice at D3 Security. Stan brings a wealth of security automation experience, having worked closely with D3 Security’s various enterprise and MSSP clients. He is the president of the Vancouver Security Special Interest Group (VanSecSIG), a not-for-profit organization.
Sign up here for the webinar. We would love to have you join us and participate in the Q&A session. For those not able to attend, we’ll be sending a link to watch the recording of the entire webinar after it ends.