Smart SOAR and Cisco Security products integrate seamlessly, providing many options for automation-assisted incident response. Smart SOAR has a range of out-of-the-box integrations tailored specifically for Cisco products. These include:
- Adaptive Security Appliance
- Email Security
- Firepower
- Identity Services Engine
- Meraki
- Orbital
- Secure Cloud Analytics
- Secure Endpoint
- Secure Malware Analysis
- Secure Network Analytics
- SecureX
- Umbrella Enforcement
- Umbrella Reporting
- Webex
This article will focus on two of the fourteen listed above: Cisco Secure Endpoint (SE) and Cisco Adaptive Security Appliance (ASA). Cisco SE, formerly known as AMP for Endpoints, offers cloud-delivered endpoint protection alongside advanced endpoint detection and response across multi-domain control points. Cisco ASA provides robust network security services that enable organizations to safeguard and monitor incoming and outgoing network traffic effectively. Smart SOAR’s integrations with these tools offer the following commands:
Cisco SE
- Create Group
- Delete File From File List By Hash
- Fetch Event
- Get Block List
- Get Computer Activity
- Get Computer By Connector
- Get Computers
- Get Groups
- Get Policy
- Isolate Computer
- List Policies
- Set File List By Hash
- Unisolate Computer
Cisco ASA
- Block IPs
- Block URLs
- Get Network Object
- Run Commands
- Test Connection
- Unblock IPs
- Unblock URLs
These commands can be used throughout the phases of the incident response cycle. The first is data ingestion. One of SOAR’s key selling points is that it centralizes all security alerts into a single platform. CSE’s Fetch Event command can be run on a schedule, pulling events into Smart SOAR as they’re generated.
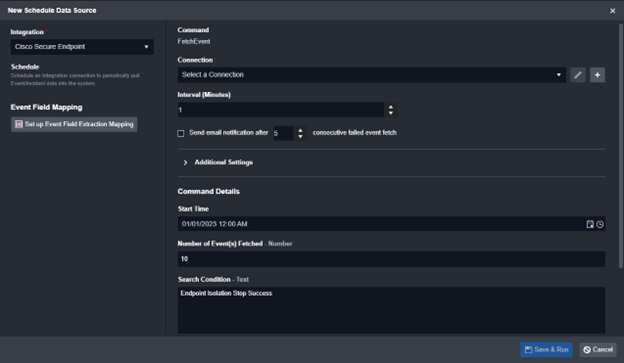
Fetch event configuration
After events have been ingested into the platform, the other commands can be used to assist with incident response in the enrichment, containment, and recovery phases.
Enrichment
Typically, in the first phase of automated workflows, enrichment-related tasks gather all relevant information and display them for the investigation team to review. The following commands are built for this stage:
- Get Block List
- Get Computer Activity
- Get Computer By Connector
- Get Computers
- Get Network Object
- Get Groups
- Get Policy
- List Policies
The Get Computers and Get Computer Activity commands retrieve valuable information about targeted devices, such as their operating system, network activity, groups, compromised status, and policies applied. The results from this search can be run through Cisco ASA’s Get Network Objects command to get details on specific IPs or URLs that devices are communicating with, and Cisco SE’s Get Groups and Get Policies to consolidate all information about the permissions associated with this device.
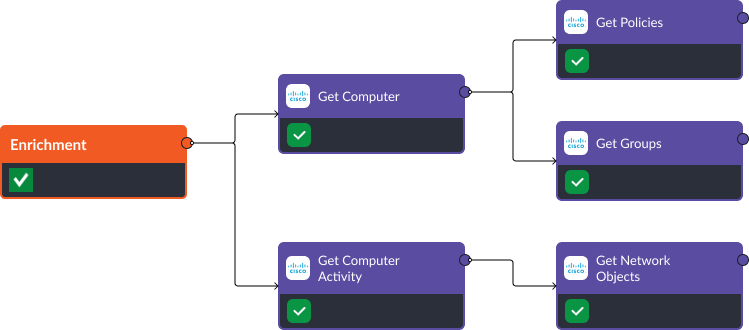
Using this information, teams don’t have to spend time retrieving all the contextual data on a security alert. Each time an event is ingested into Smart SOAR, the workflow above will trigger, automating the data collection process and ensuring teams always have relevant information for their investigation.
Containment
If the collected information indicates a breach, the Isolate Computer, Block IP, and Block URL commands can be used to quarantine an infected device and prevent any communication with suspicious targets from the network.

Recovery
Once the issue has been addressed and remediated, Smart SOAR’s recovery phase playbooks will bring devices back online and unblock artifacts using commands like Unisolate Computer, Unblock IP, and Unblock URL, restoring normal operations.

Conclusion
The integration of Cisco technologies with Smart SOAR offers organizations a multitude of options to enhance their incident response capabilities. The structured workflows demonstrated in this article serve as a foundational framework for SOAR users, enabling them to maximize the value of Smart SOAR and strengthen their team’s day-to-day security operations. With its advanced capabilities and tailored Cisco integrations, Smart SOAR emerges as the ideal choice for organizations seeking a robust, efficient, and comprehensive SOAR solution.




