-

Threat Hunting in Smart SOAR
In modern cybersecurity operations, threat hunting has become an essential proactive defense strategy. Leveraging Security Orchestration, Automation, and Response (SOAR) playbooks enhances this activity, making…
-

Stop Ransomware in its Tracks: Suspicious File Activity
The Threat Scenario Consider a scenario where your file server, “D3Cyber-FileServer,” triggers an alert. The alert indicates an encryption attempt on “important_document.docx” by the command-line…
-

Beyond One-Size-Fits-All: Advanced Playbook Triggers for Unique Use-Cases
Many SOAR users find themselves frustrated with inflexible playbook builders that often require extensive manual intervention to accommodate unique or complex workflows. Such rigidity in…
-

What it’s Like Using Integrations Built by D3
Integrating a variety of cybersecurity tools and platforms is often a complex and demanding task. This process, essential to the effective deployment of Security Orchestration,…
-

The 10 Most Common MITRE Tactics & Techniques of 2023
SOAR solutions create a centralized queue of all incidents going on in a security team’s environment. Endpoint, SIEM, email, behavior, and network alerts are all…
-

Why Smart SOAR is the Best SOAR for iZOOlogic
The collaboration between Smart SOAR (Security Orchestration, Automation, and Response) and iZOOlogic offers a comprehensive solution to protect your brand from imposters. This integration spotlight…
-
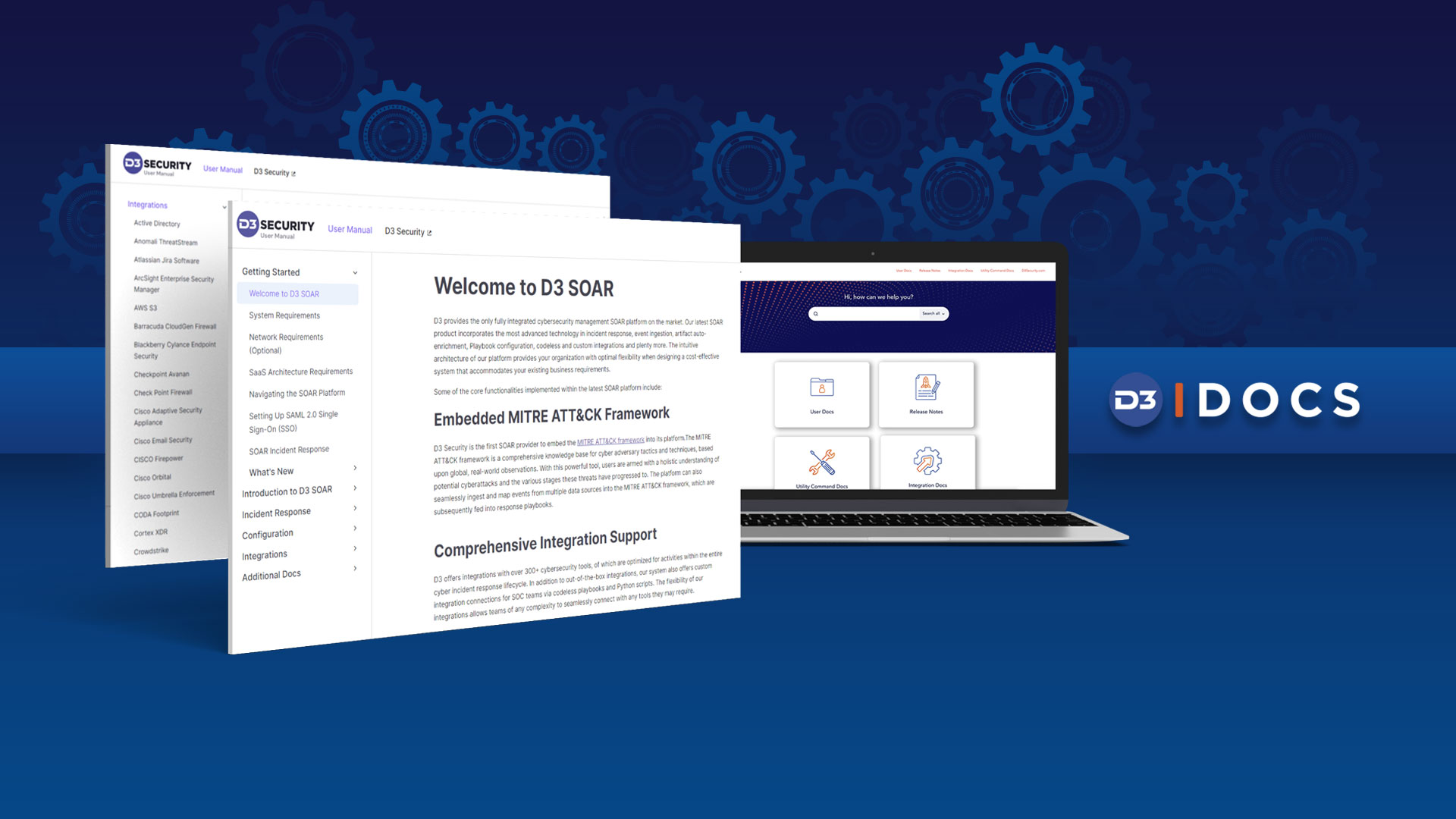
Announcing the Smart SOAR Documentation Site
We are excited to announce the launch of D3’s public documentation site. Previously, our Smart SOAR documentation was only available to our clients. Now, we…
-

The D3 Integration Development Cycle: A Journey of Precision, Innovation, and Adaptability
The quality of integrations within your SOAR (Security Orchestration, Automation, and Response) system can have a profound impact on your operational effectiveness. Recognizing this, D3…
-

The Role of Vendor-Agnostic SOAR in Overcoming Siloed Security Challenges
Siloed security refers to a situation where different security tools and processes operate independently, without effective communication or data-sharing between them. This fragmented approach is…
Pierre Noujeim
Select a term…