Every few years, security gets a new promise. SIEM was going to centralize everything. SOAR was going to automate the pain away. XDR was going to connect the dots.
Each helped. None fixed the problem. Alert volume kept rising. Stacks kept growing. Analysts stayed buried in manual work.
In a recent conversation on the Let’s SOC About It podcast, D3 Security President Gordon Benoit framed the autonomous SOC as a productivity story.
He used an analogy from folklore: “There’s this story about Paul Bunyan, a giant lumberjack who could clear forests with his ax. In the Disney animation, a man shows up with a brand new technology called a chainsaw. They have a competition. Who could clear the most trees? And lo and behold, the man with the chainsaw won.”
The lesson? “Morpheus and products like Morpheus are the chainsaw. You still need the lumberjacks, the SOC analysts. It’s just that these products are providing a chainsaw so they can do more. Significantly more.”
Why Everyone Is Talking About Autonomy Now
Interest in AI inside security didn’t start in the SOC. It started in the boardroom.
“Every organization is talking about it,” Benoit said. “You have the CEO and CFO looking for efficiencies, asking how AI can help them. That’s happening across all departments, including cybersecurity.”
Security felt that pressure immediately. Triage and incident response already run at human limits. The bottleneck is capacity.
“It’s like you went from ten analysts to a thousand analysts,” Benoit explained. “A thousand great SOC analysts. Now what can they do? When you start thinking about what’s possible with that many analysts, it gets you thinking about how many alerts you can ingest, what type of alerts, what scope of work you can throw at a product like Morpheus.”
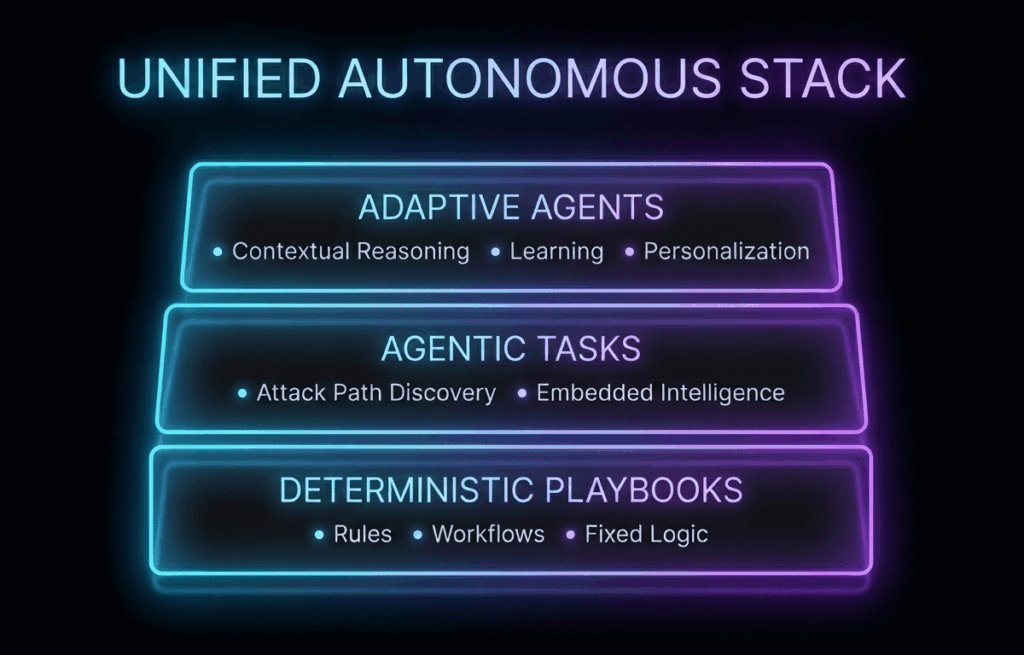
The Autonomous SOC enters the conversation as a way to change the unit economics of incident response.
The Real Problem Is Context, Not Alerts
A common objection to AI-driven triage: Can an automated system investigate with enough depth? Can it stay consistent? Can it avoid false confidence?
Benoit’s answer starts with what Morpheus does first: build an attack path.
“We ingest alerts from EDR, identity, email security, network security. We obtain the context from that alert, the IOCs. Then we take the behavior we’re able to determine and try to link behaviors across the tech stack.”
The idea is functional relationships. Each alert becomes part of a sequence of actions taken by an adversary. Those actions leave traces in different tools. Morpheus links them.
“Building the functional relationships across those gaps is where Morpheus shines,” Benoit said. “Most companies have ten, twenty products. So you have your siloed tech stack. Building relationships across those gaps; that’s where we provide a true picture.”
If there’s no attack path, the alert scores low and can close. If there is a path, the system assigns priority and confidence based on evidence.
“Not that a SOC analyst can’t do this work,” Benoit emphasized. “It’s just time. That’s the difference. If you had a SOC analyst and they had an hour for every alert, that’d be great. Morpheus runs at machine speed. It doesn’t care if it’s one alert, a thousand alerts, or 100,000 alerts.”
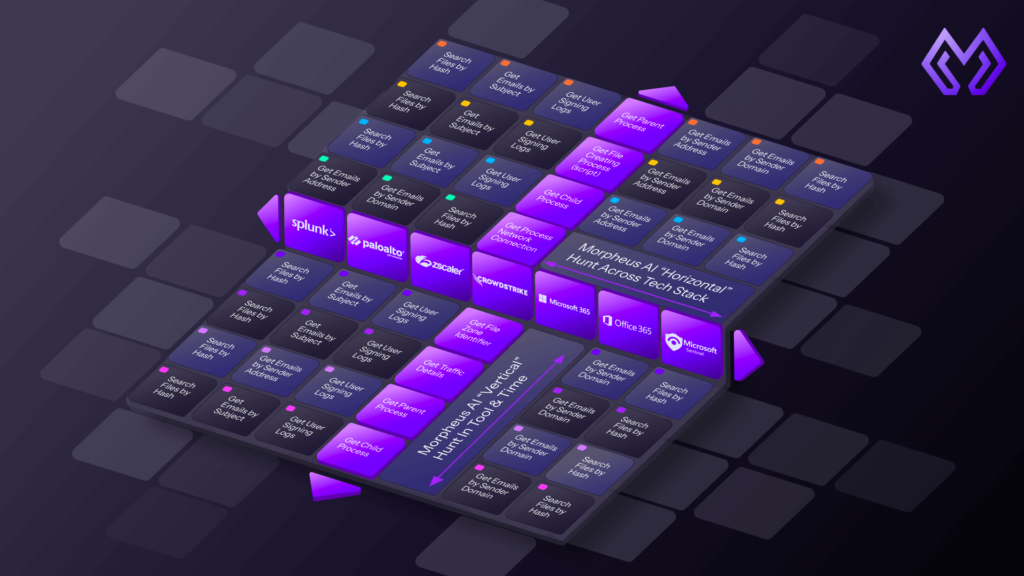
Why Frameworks Matter More Than Models
One of the more revealing moments in the conversation came from a lab experiment, where the D3 engineering team handed a raw incident to a large language model, no structure, no guidance.
“It built this incredible incident response playbook,” Benoit recalled. “The problem was Observation A was caused by a lazy developer. So it built this brilliant logic based on A,B,C,D, and it was completely wrong because Observation A was faulty.”
This is why Morpheus is more than a thin wrapper around an LLM.
“Morpheus is 70-80% framework. And 20-30% large language model,” Benoit explained. “The framework guides the large language model to build out the attack path. You can’t just take an alert and throw it into a large language model. You need to guide it.”
That framework breaks investigations into smaller, verifiable steps. It limits hallucinations. It creates repeatable outcomes.
“We’ve tested every large language model. We’ve done benchmark testing, taking incidents, putting them through Morpheus, and then having those same incidents triaged through a large language model without the guidance of the Morpheus framework. Hallucinations are real. There’s no way a company should be relying on that.”
As models improve, the framework remains the anchor. That design choice protects customers from betting their SOC on unpredictable behavior.
Drift Is the Silent Killer of Automation
Anyone who has run SOAR at scale knows the real enemy: change.
Detections change. APIs change. Playbooks break quietly.
“That’s the Achilles heel of SOAR,” Benoit said. “You have these SOAR products with API calls expecting everything to work all the time. But if a detection changes, API calls could fail. You have to spend a lot of time maintaining these products, the integrations, the flow of the playbook. And sometimes they’ll break. Your events stop flowing.”
Benoit called this problem “drift,” and it shaped Morpheus from day one.
“Morpheus ingests alerts all day long and says, ‘I know this detection.’ It knows the functional relationships. Then it gets a new detection it’s never seen. So it takes that detection, puts it through a separate stream, works on it based on context. It fixes the integration. It builds the relationships amongst the functions across the attack path.”
The goal is self-healing behavior. Alerts keep flowing and analysts don’t babysit broken workflows.
“We’re really proud of that. What it’s going to give customers is that it’s going to be self-healing. Not fragile like SOAR and XDR. They’ll have confidence that their alerts will be ingested, processed, and triaged.”
Why Analysts Trust Morpheus
Ease of use came up repeatedly in customer feedback.
“There are a lot of products on the market right now—we call them L1 bots,” Benoit said. “They focus on the L1 work but don’t have the concept of attack path. And worse, they require you to always be answering questions, always helping them. Basically building the product for them.”
Morpheus takes a different approach: “You don’t have to do that. Morpheus ingests the alert, understands the context, builds the attack path. It doesn’t keep prompting you for answers.”

Attack path is the sequence of actions an adversary takes moving through your environment. Most AI triage tools, the “L1 bots”, summarize individual alerts in isolation. They’ll tell you a PowerShell script ran on an endpoint. They won’t tell you that the same user received a phishing email 20 minutes earlier, authenticated from an unusual location, then accessed three file shares before that script was executed.
Morpheus builds the attack path by linking behaviors across your security stack. Those functional relationships turn scattered alerts into a coherent narrative: here’s how the attacker got in, here’s how they moved laterally, here’s what they touched. Without attack path discovery, you’re investigating individual puzzle pieces. With it, you see the picture.
Transparency is the second pillar of trust.
“Everything Morpheus does is in a complete log of all the logic applied to that event,” Benoit explained. “When the compliance department performs an audit, they’ll see that on every alert there’s a log of all the logic and all the steps taken. You can see its thought process. You can audit that thought process and the actions.”
That transparency matters even more during remediation. Benoit was clear: autonomous systems still need guardrails.
“If you’re running these agents and expecting them to perform remediation, that’s a big, big issue. Taking servers offline, disabling user accounts, those require human approval. The fact that we still have the SOAR product and can have approvals on remediation is extremely important.”
Playbooks Are No Longer the Product. They’re a Byproduct.
One of the more subtle shifts Benoit described involves playbooks themselves.
“A byproduct of the attack path discovery is that a playbook gets built. On the fly. No more pre-configured playbooks.”
In Morpheus, playbooks emerge from attack path discovery. The system builds contextual playbooks in response to real alerts.
“You need the context to build a playbook. Now you can build a contextual playbook. The visualization is still great—you can see everything happening, modify the logic if you want. It’s an open book.”
This flips the traditional SOAR model. Instead of engineers writing logic for future alerts, the system writes logic in response to real ones.
Scale Changes the Conversation
Morpheus was built to handle extreme volume. Benoit mentioned the ability to process 100 million alerts per day.

That number matters less on day one. It matters later, when teams add new use cases.
“Once they start using Morpheus, people are going to come up with new use cases and throw everything at it,” Benoit predicted. “You can load your vulnerability scan results. Threat intelligence reports, Morpheus can ingest those and perform actions to determine if that threat exists within your environment. Morpheus understands your tech stack.”
For MSSPs, the value is clearer.
“It’s a very tough business being an MSSP,” Benoit acknowledged. “Customer demands are sky high. But they’re not willing to pay what they should. Margins are very tight. Morpheus can help with that gross margin problem by being a force multiplier. We truly believe it will help them add more customers without adding headcount.”
Autonomy With Accountability
Autonomy without audit creates fear. AI without structure creates risk.
“For any person purchasing an AI product, that auditability is extremely important,” Benoit said.
Morpheus sits in the middle. A guided system that learns, adapts, and explains itself. A platform that acts fast but shows its work.
That’s why the Autonomous SOC is gaining traction now. Teams want their best analysts working on the problems that matter.
The chainsaw doesn’t replace the lumberjack. It lets the lumberjack clear what used to be impossible.




