While many vendors position AI as a mere helper for SOC analysts, the reality is that AI can now be the SOC analyst. It’s increasingly a better one than its human counterparts, especially in triaging alerts and routine investigative tasks. According to the latest ISC² study, the global cybersecurity workforce gap has grown 19% YoY to 4.8 million, further straining SOCs worldwide. With such a widening chasm, old ways of staffing up simply aren’t sustainable anymore.
The Hard Truth About SOC Analysts Today
Let’s be honest about the current state of security operations. Even your best Tier 3 analysts can only fully investigate 20–30 alerts per day. The rest? They receive a cursory review or get dismissed based on simple rules.
We’ve built elaborate hierarchies of tiered analysts, but much of their time is spent on mechanical, repetitive tasks like querying systems and compiling reports. In many real-world SOCs, budget constraints and overwhelming alert volumes leave countless suspicious events uninvestigated. The uncomfortable truth is that even at senior levels, many analysts aren’t doing truly sophisticated work because they lack the time, not necessarily the talent.

Beyond “AI-Assisted”—The AI SOC Analyst
The next evolution isn’t about AI helping analysts, it’s about AI being the analyst in key operational areas. An AI SOC analyst can process every single alert, not just a sample. While a human analyst might perform a dozen investigative steps, AI can execute hundreds, searching simultaneously across email, network, identity, and endpoint data, in addition to CVE, TI, and TTP sources, For an AI analyst, there is an entire world of context available, unfathomable in scope and unworkable for people.
It can dive deep into a single system or hunt broadly across your entire security stack, documenting every step of its logic for review and improvement. Crucially, human oversight remains essential to guide AI decisions, refine investigative playbooks, and handle truly complex or novel attacks.
Breaking Down the Tiered Analyst Model
In traditional Security Operations Centers (SOCs), analysts are organized into a hierarchical tier structure, typically ranging from Tier 1 to Tier 3. Each tier requires progressively more experience and expertise, with analysts advancing through the ranks as they gain skills:
- Tier 1: Alert triage, basic monitoring, and incident prioritization
- Tier 2: Deeper investigation, threat analysis, and response coordination
- Tier 3: Advanced threat hunting, malware analysis, and strategic recommendations
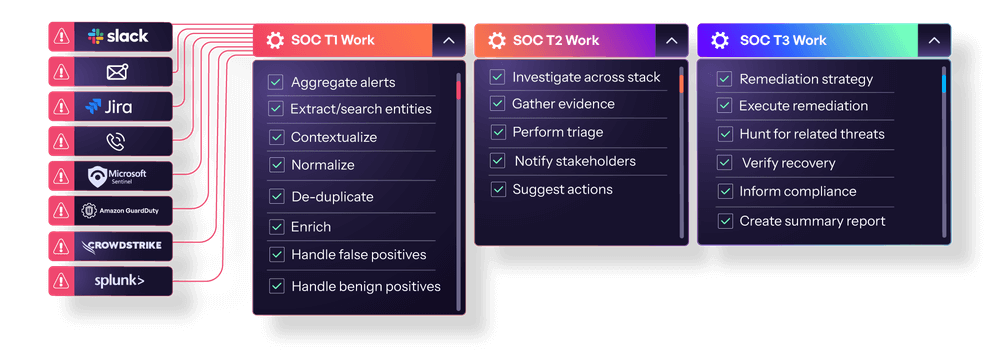
The AI SOC analyst challenges this traditional model. An autonomous SOC solution like D3 Morpheus can replace some of the tasks typically assigned to Tier 1 and Tier 2 analysts, performing a level of Tier 3-level analysis on every alert. Most importantly, it scales infinitely without adding headcount.
What This Means for Security Teams
Morpheus autonomously triages, investigates, and responds—handling 95% of alerts in under 2 minutes. This means security teams can be smaller but more strategic. Every alert receives a thorough, automated investigation. Coverage expands across the entire security stack. This doesn’t eliminate the need for skilled human analysts; instead, it allows them to focus on the investigations that truly require human judgment. And they can use human judgement to push the AI further, prompting deeper analysis, querying bespoke data, uncovering more stealthy behaviors, hence making your organization more contextually aware and resilient.

Costs decrease while effectiveness increases. Future security teams will focus on strategy and architecture, reviewing and tuning AI and automation logic, engaging in advanced threat hunting, and driving security innovation. The grunt work of alert processing gives way to genuine security leadership.
Time to Think, And Act, Differently
While others debate whether AI can match human analysts, we’ve built something that bridges gaps in large-scale alert processing and fundamentally transforms security operations. D3 Morpheus can process millions of alerts daily, leveraging an entire world of context, bringing hundreds of data points into consideration, for every single alert, and executing hundreds of investigative steps where humans manage only dozens.
This isn’t theoretical—it’s operational. D3 Morpheus is already hunting threats across email, network, identity, and endpoint systems simultaneously, performing both deep vertical analyses within individual tools and broad horizontal investigations across your entire security stack. It’s finding attack paths humans miss, calling the right API functions without without forcing you to dig through documentation, and orchestrating responses with consistent, high-speed precision, night and day and on the Christmas Eve or 4th of July. Every step is documented, every decision explained, and every response is customizable to your environment.
By combining AI-driven automation with expert human input, you can maintain trust in your findings and confidence in your processes. The future of security operations is here—it’s just not evenly distributed yet. Ready to see what a true AI-augmented analyst can do? Schedule a demo with our team today.




