For decades, Security Operations Centers (SOCs) have operated within a tiered framework:
- Tier 1 (L1): Junior analysts handle alert intake and triage
- Tier 2 (L2): Analysts investigate suspicious activity and escalate when needed
- Tier 3 (L3): Senior analysts lead incident response and proactive threat hunting
- (Some even refer to Tier 4 as their elite hunt and CTI team)
While this structure helped formalize workflows and career paths, it also locked the SOC into some tough trade-offs:
- L1 analysts drown in noise (40% of alerts are never investigated)
- L2 analysts spend more time stitching logs than stopping threats while phishing-led breaches can succeed in <1 hour.
- L3 analysts become bottlenecks
- Turnover is high, and burnout is everywhere (84% of workers reported experiencing stress, fatigue, and burnout.)
It’s time for an upgrade.
Morpheus Automates L1 and L2, So Analysts Can Do the Work That Matters
Morpheus completely automates Tier 1 and Tier 2 operations.
This means:
- Every alert is automatically investigated and triaged
- Every IOC is enriched, correlated, and contextualized
- Noise is suppressed at the root, not just filtered
What’s left for human analysts is the high-value work:
- Interpreting results
- Identifying patterns across cases
- Strategizing next steps
- Engaging with threat intelligence and response planning
Instead of chasing down logs and manually pasting hashes into search consoles, analysts start with a full case file, curated and documented in Morpheus’s Analyst Workspace.
How It Works: A 360° Investigation Framework
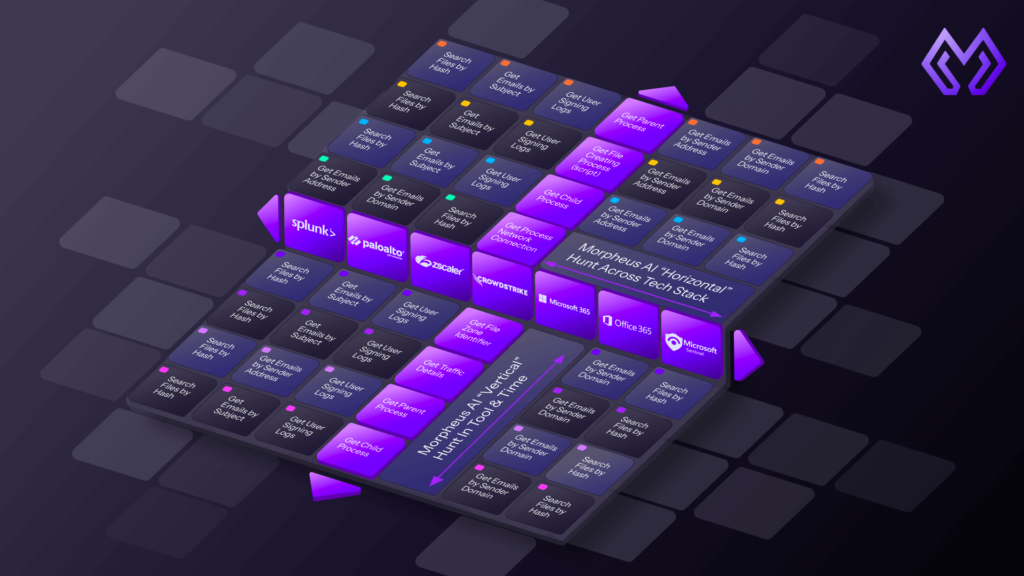
Morpheus ingest alerts and proactively investigates them using a unique Deep Research framework that includes:
- North-South telemetry: Visibility into external connections, command-and-control patterns, and data exfiltration
- East-West correlation: Mapping movement across systems, accounts, and endpoints inside your environment
- Temporal enrichment: Pivoting backward in time to build timelines and detect earlier stages of an attack
- Autonomy With Guardrails: Deterministic guidance keeps logic explainable, auditable, and modifiable.
This ensures that every investigation is complete, reliable, and free of data gaps that plague traditional alert triage.
What This Means for Analysts: Better Work, Less Burnout, More Growth
There’s a lot of fear in the industry that AI will replace SOC analysts.
But Morpheus is built to empower them.
✅ No More Burnout
- Morpheus handles the repetition
- Analysts handle the decisions
- No more 2 AM alert storms or alert queues that never end
📈 Upskill your Talent
- Junior analysts start by analyzing fully enriched cases, not raw telemetry
- They learn by reviewing automated investigations and outcomes
- They move into higher-value work faster, like threat hunting, red team support, or cloud security
🔁 Scale With the Team You Already Have
- You don’t need to hire 3x as alert volume grows
- One empowered analyst can oversee what used to take a team
- Your current team grows more capable, and more fulfilled
Instead of being replaced by automation, analysts move up the value chain, delivering better insights, faster decisions, and stronger defenses.
A Smarter SOC for the Future
When Morpheus is deployed:
- L1 is eliminated: Fully automated, zero queue
- L2 is optional: Reserved for special cases
- L3 becomes the focus: Empowered with instant context and guided decision support
The human capital in your SOC gets better, faster, and stronger, instead of being ground down by busywork.
The Queue Stops Here: Full Coverage Without Burnout
Security teams are tired. The queue never ends. Alerts don’t stop.
With Morpheus, smart humans stay central, but their time shifts from grunt work to strategy, hunting, and defense design. Analysts get clear cases instead of noise, and leaders get a defensible, predictable cost model. For executives, the impact is measurable: faster containment, lower breach losses, and higher analyst productivity.
Want to see how Morpheus modernizes your SOC while uplifting your team? Book a demo now.




