Security automation playbooks are powerful when properly governed. They can quarantine endpoints, block malicious IPs, disable accounts, or even orchestrate full-scale incident response in minutes, provided they are tested and scoped appropriately.
If they aren’t, they can be dangerous. One misconfigured regex can isolate half your fleet. A missing approval can take down critical services. And in the middle of an incident, the temptation to “just hotfix it in prod” is strong, but risky.
This is why your playbooks deserve the same discipline as any other production software. Enter: CI/CD for security automation.
Why CI/CD Belongs in Security Automation
A continuous integration/continuous delivery (CI/CD) pipeline enforces safe, consistent, and auditable changes to your playbooks. Benefits include:
- Safety by design – Syntax checks, linters, unit tests, dry-runs, and integration tests in a sandbox catch errors before they reach production, shifting security left in the development lifecycle.
- Reproducibility & rollback – Versioned artifacts mean you can promote the same signed playbook through dev → staging → prod, and instantly revert if something goes wrong.
- Auditability & compliance – Every change has a pull request, reviewer approvals, test evidence, and deployment logs—ideal for SOC 2, ISO 27001, and forensics.
- Governance & separation of duties – Code owners, protected branches, and mandatory reviews prevent rogue or risky changes.
- Secure secret handling – Pipelines integrate with a vault to inject short-lived credentials at runtime, eliminating hard-coded keys.
- Environment parity & drift control – Declarative infrastructure and automated deployments keep dev, staging, and prod consistent.
- Supply chain security – SBOM generation, dependency pinning, vulnerability scanning, and artifact signing reduce exposure to third-party risks.
- Controlled rollout – Canaries and feature flags limit the blast radius of changes.
- Faster, safer hotfixes – When incidents hit, automated validation ensures you can ship fixes without panic.
- Operational metrics – CI/CD surfaces deployment quality metrics to guide continuous improvement.
Anti-Patterns CI/CD Prevents
In security automation, anti-patterns are habits, such as editing playbooks directly in production or skipping tests, which seem efficient but invite errors, outages, or vulnerabilities. CI/CD is your shield against these disasters.
| Anti-Pattern | Risk | CI/CD Control |
| Editing playbooks directly in prod | Typos or unreviewed changes cause outages or compliance violations; no audit trail for regulatory scrutiny. | Protected branches, signed artifacts, read-only prod. |
| “Snowflake” environments | Playbook works in dev but fails in prod due to drift. | Infra-as-code, immutable runners, drift detection. |
| Untracked hotfixes | No rollback path, unclear changes during incidents. | Break-glass PR path with approvals; versioned artifacts. |
| Long-lived or hard-coded secrets | Keys leak, granting persistent attacker access. | Vault integration, short-lived credentials, secret scans. |
| Copy-paste playbooks per team | Drifting forks, inconsistent containment. | Reusable modules, promotion pipelines, policy tests. |
| No schema or policy validation | Malformed YAML/JSON or risky commands slip through. | Schema validation, linting, policy-as-code checks. |
| Untested integrations | API changes or limits break response actions. | Integration tests with mocks, canary deploys. |
| Hidden dependency drift | Upstream library changes cause unexpected failures. | Dependency pinning, SBOM, signed builds. |
| Monolithic releases | One bad change impacts the whole SOC. | Feature flags, staged rollouts, auto-rollback. |
| No rollback path | Failures cause prolonged downtime or wrong remediations. | Previous artifacts kept, one-click rollback. |
| Logging as an afterthought | Poor forensics and change visibility. | Structured deployment logs, PR-to-release mapping. |
| Ad-hoc deployments | Quality depends on who’s on shift. | CODEOWNERS, mandatory approvals, change windows. |
| “Works on dev, fails on prod data” | Regexes/parsers fail on messy real-world events. | Replay sanitized real events in CI tests. |
| Manual documentation | Docs lag reality, causing bad on-call responses. | Auto-generated runbooks and changelogs from pipeline. |
| No kill switch | Runaway containment (mass isolation). | Feature flags, scoped rollout, safety switches. |
What a Great Security Playbook Pipeline Looks Like
A robust CI/CD process for security playbooks should mirror the rigor of modern software engineering pipelines, adapted to the high-stakes nature of incident response. In an ideal state, the pipeline enforces quality, security, and governance from the moment an idea becomes code, all the way to its controlled release in production.
- Data-Contextual Design
Playbook development begins with a thorough understanding of the incident patterns it will address, grounded in real alert structures, detection logic, and environmental context. This ensures workflows are relevant and operationally aligned from the outset. - Pre-Commit and Local Validation
Before any change leaves a developer’s or analyst’s workspace, automated checks scan for secrets, enforce schema compliance, and validate against organizational coding standards for automation logic. Early failure here prevents costly mistakes later. - Automated Self-Testing
Each playbook undergoes unit tests on individual components and integration tests across its workflow, simulating both the alert flow and the remediation steps. Failures trigger notifications for manual review, with clear visibility into test results. - Version Control and Peer Review
Changes are committed to a version-controlled repository. The pipeline triggers a pull request workflow requiring human review, ensuring separation of duties and accountability. Reviewers can trace each modification to the originating alert pattern or operational requirement, and generate accurate changelogs for compliance and operational use. - Staging Deployment and Safe Mode
Playbooks are deployed to a non-production environment, processing live or replayed incident data in a no-impact “dry run” mode. This allows observation of decision points, response logic, and potential side effects without risking unintended production actions. - Progressive Rollout
Once approved, deployments proceed to production in controlled phases, starting with a limited scope or subset of endpoints, then gradually expanding. Telemetry is monitored for anomalies, with automated rollback triggered on error thresholds. - Post-Deployment Validation and Metrics
After release, the pipeline captures operational metrics: automation coverage, false-positive impact, average time to resolution, feeding them back into the SOC’s observability layer. This creates a closed feedback loop for continuous refinement.
This kind of pipeline treats security playbooks as living code artifacts subject to the same reliability, safety, and audit requirements as any production system, while remaining tuned to the time-critical realities of incident response.
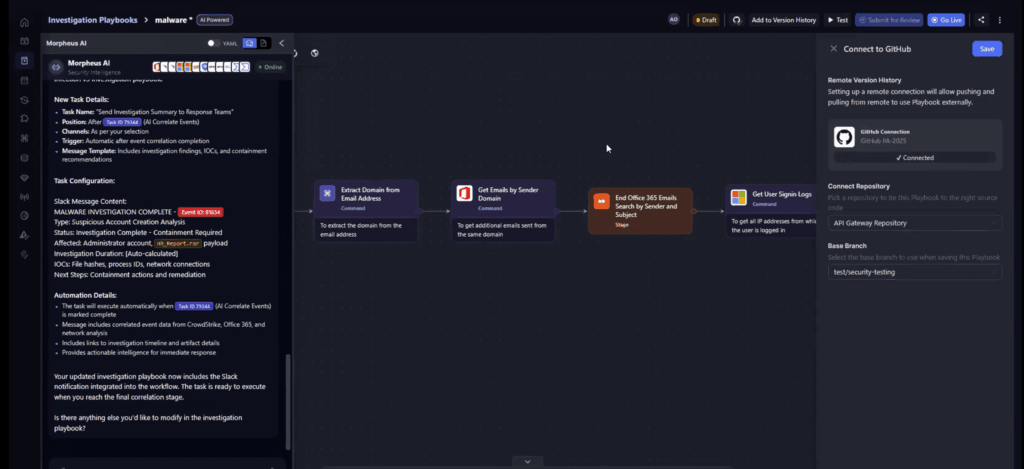
How Morpheus Delivers End-to-End CI/CD for Security Playbooks
Everything we’ve discussed about bringing CI/CD discipline to security automation, Morpheus already bakes it in.
With GitHub synchronization, every playbook is version-controlled, tested, and reviewed before hitting production. The platform’s automated self-testing runs unit and integration tests on AI-generated playbooks, applies fixes automatically, and only allows submission for review once all checks pass. Integrated approval workflows push pull requests straight to your chosen repository for human sign-off, ensuring that governance and separation of duties are preserved.
From field mapping alerts from active data sources to AI-assisted playbook generation and step-by-step configuration via an interactive AI assistant, Morpheus turns automation from risky scripts into reliable, governed workflows.And because it’s tied to a modular SOC manager/CISO dashboard, you’re also tracking key performance indicators like automation coverage, false-positive rates, backlog, and resolution metrics in real time. That means every improvement in your pipeline is measurable, auditable, and tied to actual risk reduction.
See how end-to-end CI/CD for security playbooks can reduce your response risks. Book a Morpheus demo and assess your current pipelines against these best practices today.




