Our latest update to Smart SOAR brings in a wealth of enhancements aimed at streamlining cybersecurity management for enterprises. A notable feature in this release is the ability to view credentials while editing them, for easier password entry and verification across various modules. We’ve also rolled out enhancements to our ‘Correlate Events’ utility command, to enable efficient incident management.
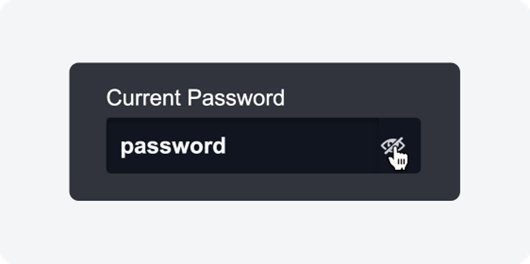
View Credentials While Editing
In select areas within D3 SOAR where credential modifications are required, a visibility toggle icon (depicted as an eye icon) has been introduced to aid in password entry and verification. This feature has been deployed across various areas of the platform, as listed below:
- Preferences: Under the “Change Password” option.
- Organization Management: Navigate to “Users” then “Change Password.”
- Connections Module: While creating or editing a connection.
- Integration Configuration: While creating or editing connection credential parameters and Password Vault connections.
- Playbook Editor: While creating or editing a connection within a command task with an integration command.
Please note that once a password has been saved, the eye icon will not be available when revisiting the credentials. To re-activate the visibility toggle, you must clear the existing password entries and re-input the passwords.

Utility Command Enhancement
Correlate Events: Associated Incident Numbers Added to Output Context Data
The updated Correlate Events utility command now returns incident numbers linked to the correlated event in the output Context Data. This is particularly useful when events have been escalated to incidents, and there’s a need to consolidate multiple events into a single incident.
Previously, while correlated events could be grouped together, the corresponding incidents needed to be closed individually. With the inclusion of incident numbers alongside correlated events, you now have the ability to bulk-close related incidents with subsequent playbook tasks.
Enhanced Query Functionality in Event and Incident Management Utility Commands
We have improved the Search Condition parameters for the following event and incident management utility commands:
- Link Event to Incident
- Link to Related Event Incident
- Update Identical Event
- Trigger Incident External Action
Previously, functionality of the Search Condition for event and incident queries was limited to exact matches on event or incident fields as demonstrated below.
{
"EventType": "aaa",
"__CustomField": "bbbb"
}
It does not extend support for more advanced query operations such as comparisons (greater than or less than), time range specifications, ‘In’ operator usage, or regular expression matching.
With the new enhancement, the Search Condition parameters now support a broader spectrum of query syntaxes and capabilities such as range queries, regex matching, and more. You can seamlessly filter incidents based on attributes like type, status, severity, or a specific date range, among other criteria.
For example:
{
"Type": "Phishing",
"Status":"Open",
"Severity": { "$in": ["Critical", "High"] },
"Title": { "$regex": "email", "$options": "i" }
}
Or
{
"CreatedUtcTime": {
"$gt": {
"$date": "2023-08-01T00:00:00Z"
},
"$lt": {
"$date": "2023-08-08T00:00:00Z"
}
},
"ExternalKey": { "$regex": "^Phishing" }
}
These examples show how the enhanced Search Condition parameters can be utilized with the new enhancements to precisely find your incident and event data to perform command actions.
Creating a File from Input Text Array: Added Support for HTML Files
The Create a File from Input Text Array utility command has been enhanced to support HTML file generation using a text array input. To do this, simply select ‘HTML’ as the Output Type when configuring the command’s input parameters.




