Here’s a quick walkthrough of the latest features and enhancements in the June 2023 release of Smart SOAR. With a complete overhaul of the Reporting & Analytics dashboard, an innovative MSSP Client Portal, significant incident workspace improvements, and much more, this update promises to elevate your security orchestration, automation, and response capabilities to new heights. Let’s dive into the specifics and explore how these updates will streamline your security operations and empower data-driven decision making.
Reporting Dashboard Revamp
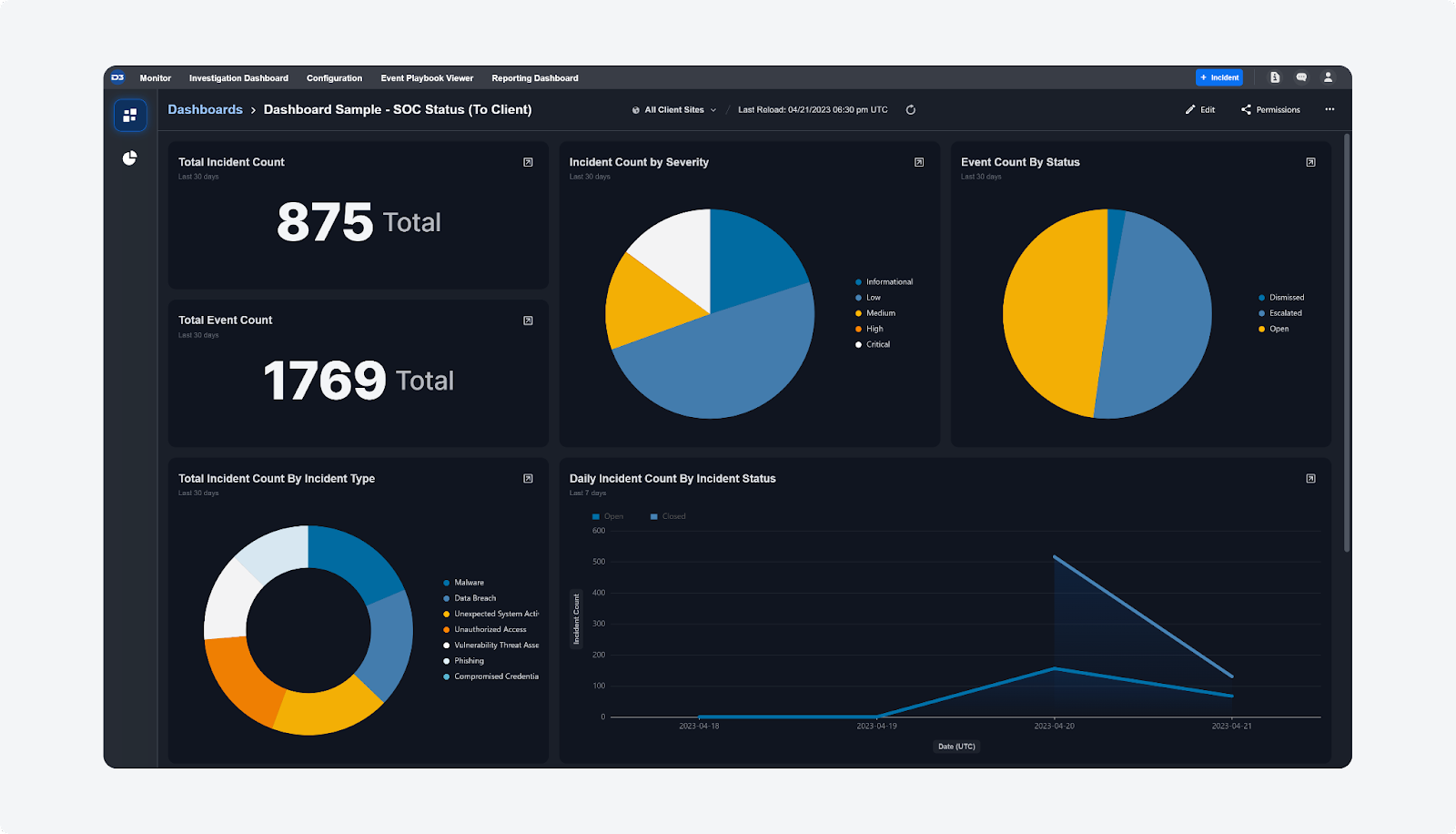
The Reporting & Analytics dashboard module has been completely revamped into the Reporting Dashboard, with a new user interface and new functionalities. The new reporting features offer personalized dashboards to security executives and managers to visualize and monitor their Key Performance Indicators (KPIs) in real time.
This module comprises two main parts: Widgets and Dashboards.
Widgets extract and visually represent data from four key sources: Artifacts, Events, Global Lists, and Incidents. You can build queries using the query builder to extract data from these sources and select specific time ranges and sites to display within the widget. Once created, these widgets can be added to Dashboards.
Dashboards are collections of widgets that can be tailored to meet different reporting needs, including KPI monitoring, (service level agreement) SLA monitoring, and (security operations center) SOC team management. The dashboard view can also be filtered by sites and time range and exported as images in the PNG format.
In addition, you can use the email scheduler feature to automate the sharing of dashboards, by conveniently scheduling one-time or recurring emails to recipients. Recipients get a link in the email, allowing them to access the interactive dashboard without additional logins, streamlining communication and supporting data-driven decisions.
MSSP Client Portal
The MSSP (Managed Security Service Provider) client portal is an innovative addition enhancing communication, visibility, and collaboration between MSSPs and their clients.
Once the license for the client portal is purchased and activated, MSSPs can create user accounts with customized roles specifically designed for their clients. These roles, configured with the “Client” access type, provide MSSP clients with limited access to the SOAR platform, including the investigation dashboard and reporting dashboard. Here are the key features:
- Incident Review: Allows clients to view both summarized and in-depth incident details of incidents and events from the investigation dashboard.
- Interaction Capabilities: Clients can perform specific actions, such as running ad hoc commands and responding to tasks requiring SLA approvals.
- Messaging: MSSPs can use the portal to communicate with their clients and request approvals, improving response times and facilitating collaboration.
- Reporting and Analytics Dashboard: MSSPs can provide clients with valuable insights into their security operations through curated reports and data visualizations.
- Investigations Tab: Clients can view insights on each incident curated by the MSSP, organized by Summary, Findings, Mitigations, and Recommendations.
The client portal serves as a centralized hub that consolidates essential functionalities for efficient and effective collaboration. It empowers MSSPs and their clients to interact, share information, and work together towards their security goals.
Incident Workspace Enhancements
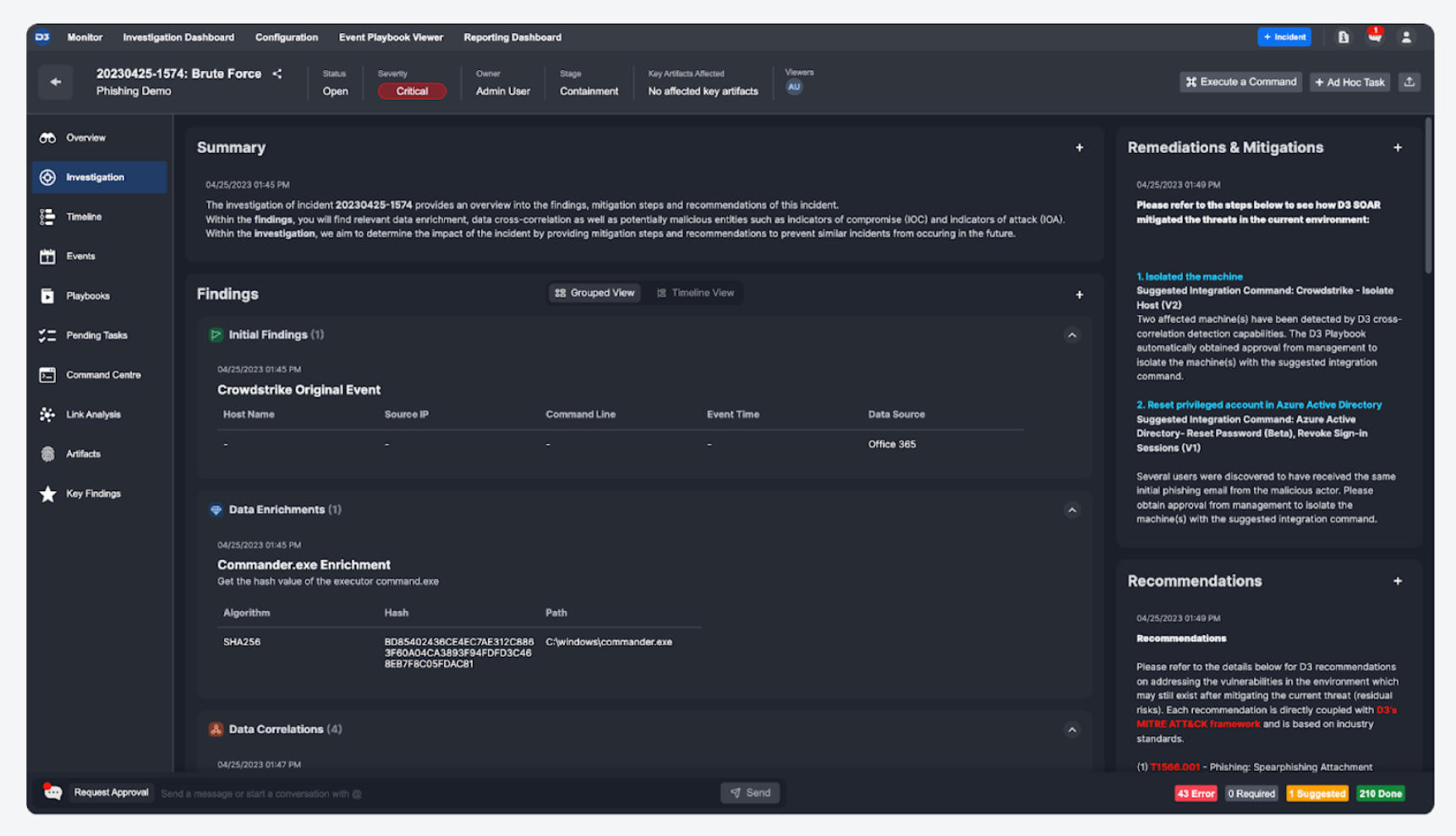
Investigations Tab
The Investigations Tab is a brand new section added to the Incident Workspace.
This tab, a centralized location, is designed for analysts. They can use it to input and manage investigation information related to an incident. It consists of four sections: Summary, Findings, Remediations & Mitigations, and Recommendations. Here, analysts can log details such as notes, findings, and recommendations using data tables defined by JSON or HTML.
The Findings section has further subsections: Initial Findings, Data Enrichments, Data Correlations, Indicators of Attack (IOA), and Indicators of Compromise (IOC). Analysts can choose between manual input or automated data population using utility commands in playbooks, thus saving time and ensuring precise capture of crucial details.
Data Ingestion
MITRE TTP Search and Event Automation Rules Settings
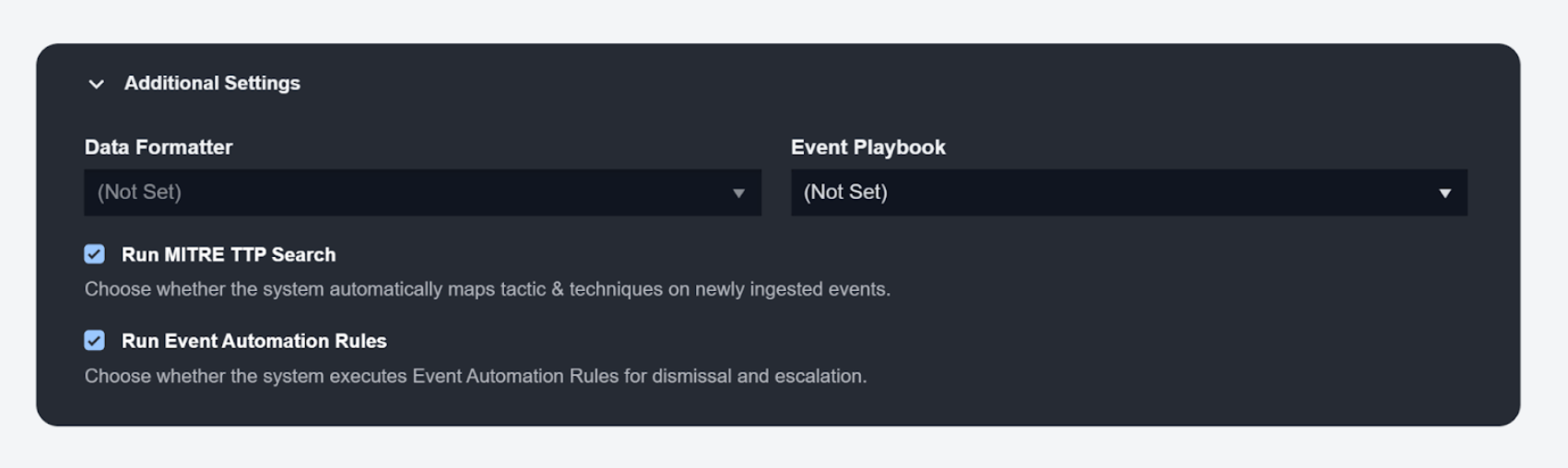
Two checkboxes will appear when configuring a new data source across these components:
- API Keys
- JSON Web Tokens (JWT)
- Data Ingestion
- Schedule
- Upload File (from the Investigation Dashboard)
- Ongoing Surveillance Task
These checkboxes offer customization options for the behaviour of ingested events. The first checkbox enables the automatic mapping of ingested events from the data source to MITRE tactics and techniques. The second checkbox enables event automation rules for event dismissal and escalation.
JWT Authentication

JWT is an open and widely accepted industry standard, defined in RFC 7519. JWTs offer a secure and efficient method for transferring claims between two parties, ensuring the data’s authenticity and integrity. In D3 Smart SOAR, you can now use JWTs to authenticate data ingestion and remote commands via webhook. Additionally, you can reassign, regenerate, rename, and delete tokens as needed.
To enable JWT authentication in D3 Smart SOAR, follow these steps:
- Navigate to Configuration > Application Settings > Web Config
- Set the value of the “EnableEnhanceWebhookAuthentication” configuration key to True.
IOA/IOC Link Analysis
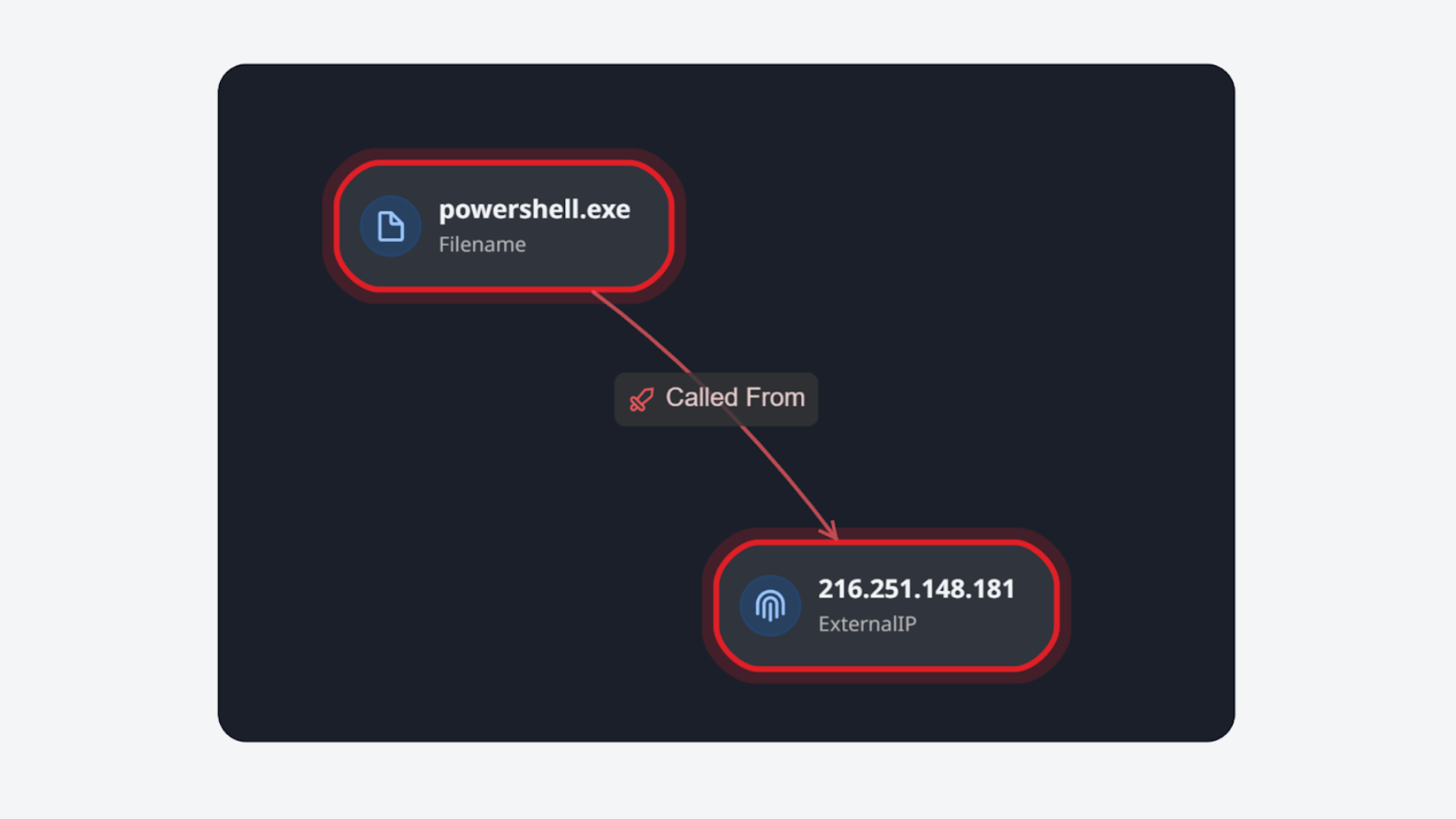
In the IOA/IOC Link Analysis tab of the Investigation Dashboard, Smart SOAR visualizes the relationships between Indicators of Attack (IOAs) and Indicators of Compromise (IOCs) extracted from events and incidents. You can view analyses from the past 7 or 30 days to get insights on historical attack patterns.
Each node in this analysis represents an artifact entity. We use color coding to distinguish between the entities: red indicates an IOA, yellow an IOC, and a combination of both signals than an entity is both. The arrows in the analysis diagram reveal the direction of the relationship labelled on them.
By clicking on a node, users can access additional information. For automated link analysis, the “Add Investigation Details” command provides users the ability to define the relationships between artifacts.
Incident Playbook Enhancements
Trigger: On Incident External Action
The On Incident External Action trigger, found in incident playbooks, is designed to merge external action data with raw incident data. This facilitates comprehensive investigations of incidents, following a defined playbook workflow. To use this, users input events through the D3 API, each identified by a unique key. Should multiple requests share the same key ID, the system will group them into a single incident. Importantly, the trigger feature provides the capability to launch additional workflows for examining a specific incident, avoiding the need for direct login into D3 Smart SOAR.
Connections Module Enhancements
The Connections Module now features an added Webhook Keys tab, enhancing its ability to to efficiently manage and view all the webhook keys linked to your account. This addition holds particular value for our MSSP users, tasked with managing webhook keys across various client sites and tenants. The Webhook Keys tab allows users to centrally access and delete keys created from their account, streamlining the key management process.
Application Settings Enhancements
Dashboard Columns
This new update enhances your user experience by offering improved management of default and custom columns in your investigation dashboard. When you add a new custom column, it will be automatically saved to the investigation dashboard. To enable or disable the column, simply click the “more” icon located on the top right corner of event and investigation lists.
Logo Customization
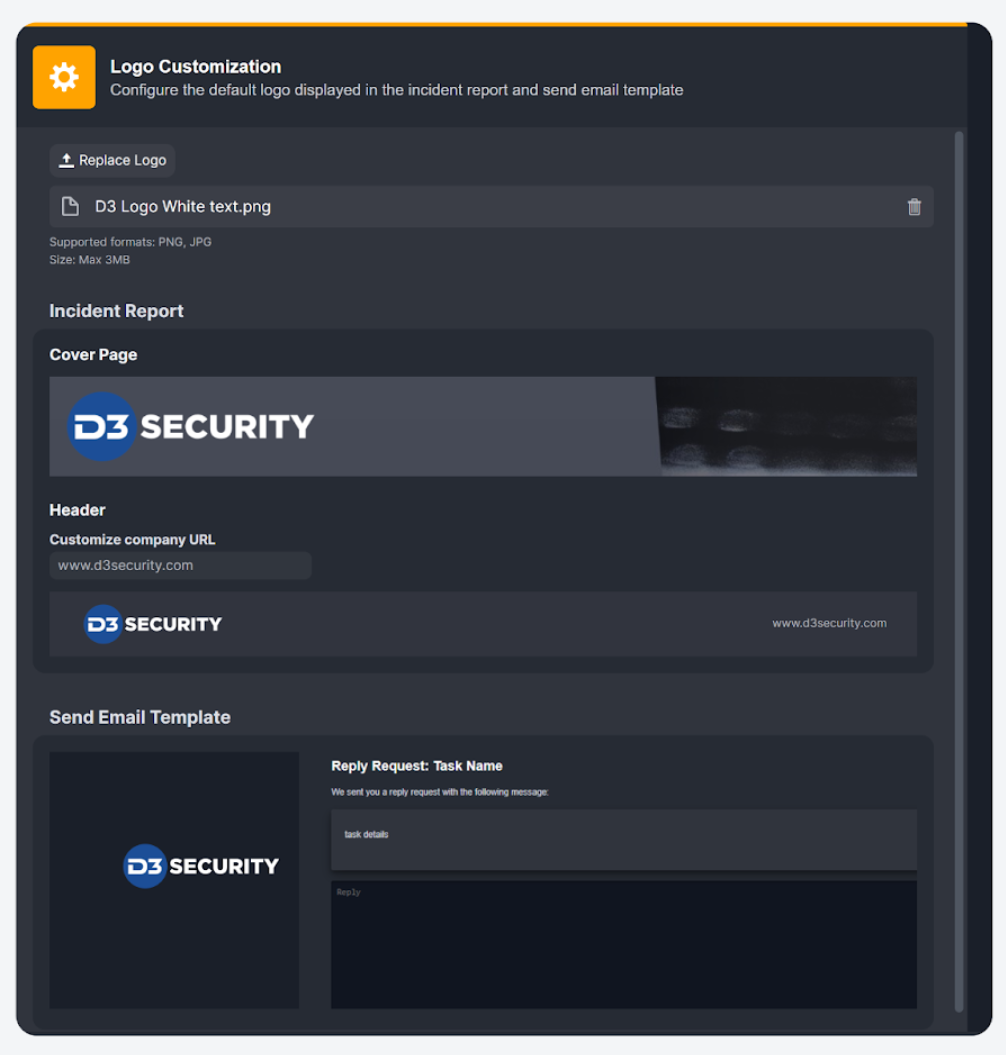
Customize the branding of your incident reports and email approval pages to better reflect your company or MSSP’s corporate identity.
By default, the incident report and send email templates are equipped with D3’s logo. You now have the option of uploading your own logo to replace the default. You can also include your company URL in the incident report header.
Integrations
New Integrations
The following integrations have been added to D3 Smart SOAR in this release.
| Integration Name | Description |
| CrowdStrike Falcon Intelligence | Crowdstrike Falcon Intelligence enables organizations of all sizes to better understand the threats they face and improves the efficacy of their other security investments with actionable and customized intelligence to defend against future attacks, making proactive security a reality. |
| CrowdStrike Threat Graph | CrowdStrike Threat Graph is the brains behind the Falcon cloud-native platform. The CrowdStrike Security Cloud leverages Threat Graph to correlate trillions of security events per day with indicators of attack, threat intelligence and enterprise telemetry from across customer endpoints, workloads, identities, DevOps, IT assets and configurations. The CrowdStrike Security Cloud creates actionable data, identifies shifts in adversarial tactics, and maps tradecraft in the patented Threat Graph to automatically prevent threats in real-time across CrowdStrike’s global customer base. |
| CyberInt | Cyberint, the Impactful Intelligence company, fuses threat intelligence with attack surface management, providing organizations with extensive integrated visibility into their external risk exposure. Leveraging autonomous discovery of all external-facing assets, coupled with open, deep & dark web intelligence, the solution allows cybersecurity teams to uncover their most relevant known and unknown digital risks – earlier. |
| D3 Tool Kit | D3 toolkit is a collection of software development tools and resources that help developers increase their productivity and efficiency, improve the quality of their applications, facilitate collaboration among team members, and stay up-to-date with the latest technologies and trends in software development. |
| Kaspersky Security Center OpenAPI | Kaspersky Security Center takes the complexity out of security administration and IT systems management. The API is for controlling Kaspersky Security Center administration tools. It also allows integration with the ability to periodically retrieve detailed information about events. |
| Microsoft 365 Defender (Email & Collaboration) | Microsoft 365 Defender, part of Microsoft’s XDR solution, leverages the Microsoft 365 security portfolio to automatically analyze threat data across domains, building a complete picture of each attack in a single dashboard. This integration allows organizations to fetch security incidents, update security incidents and run advanced hunting queries to inspect unusual activity, detect possible threats, and even respond to attacks. D3’s integration for Microsoft 365 Defender (Email & collaboration) is using Exchange Online PowerShell to provide the operation on the Tenant Allow/Block list, which allows the user to Allow/Block email addresses, domains, URLs, and files. |
| Recorded Future – SecurityTrails | SecurityTrails is a total inventory that curates comprehensive domain and IP address data for users and applications that demand clarity. By combining current and historical data of all Internet assets, SecurityTrails is the proven solution for 3rd-party risk assessment, attack surface reduction and threat hunting. This integration enables organizations to query risk issues and correlate domain and IP address data for risk assessment and threat hunting. |
| Screenshot Machine | The Screenshot Machine captures a full-page screen or small website thumbnail or to create a PDF from web pages online. |
| Sevco | Sevco is an Asset Intelligence platform to aggregate inventory of users and devices and the relationships between them and monitor the changes over time. This product is a newly identified Cybersecurity Asset Attack Surface Management (CAASM) as an emerging technology focused on enabling security teams to solve persistent asset visibility and vulnerability challenges. |
| Sucuri SiteCheck | Sucuri SiteCheck scanner remotely checks any URL for security threats, malware, defacements, out-of-date CMS, blacklisting, and other important security issues. It visits a website like an everyday user would to verify the source code for malicious behaviour or security anomalies. |
| unshorten.me | Unshorten.me is a free service to Un-Shorten the URLs created by URL shortening services. Unshorten.me can un-shorten URLs created by different services like goo.gl (Google), fb.me (Facebook), t.co (Twitter), bit.ly, TinyURL, ow.ly, among others. |




