MITRE ATT&CK + SOAR






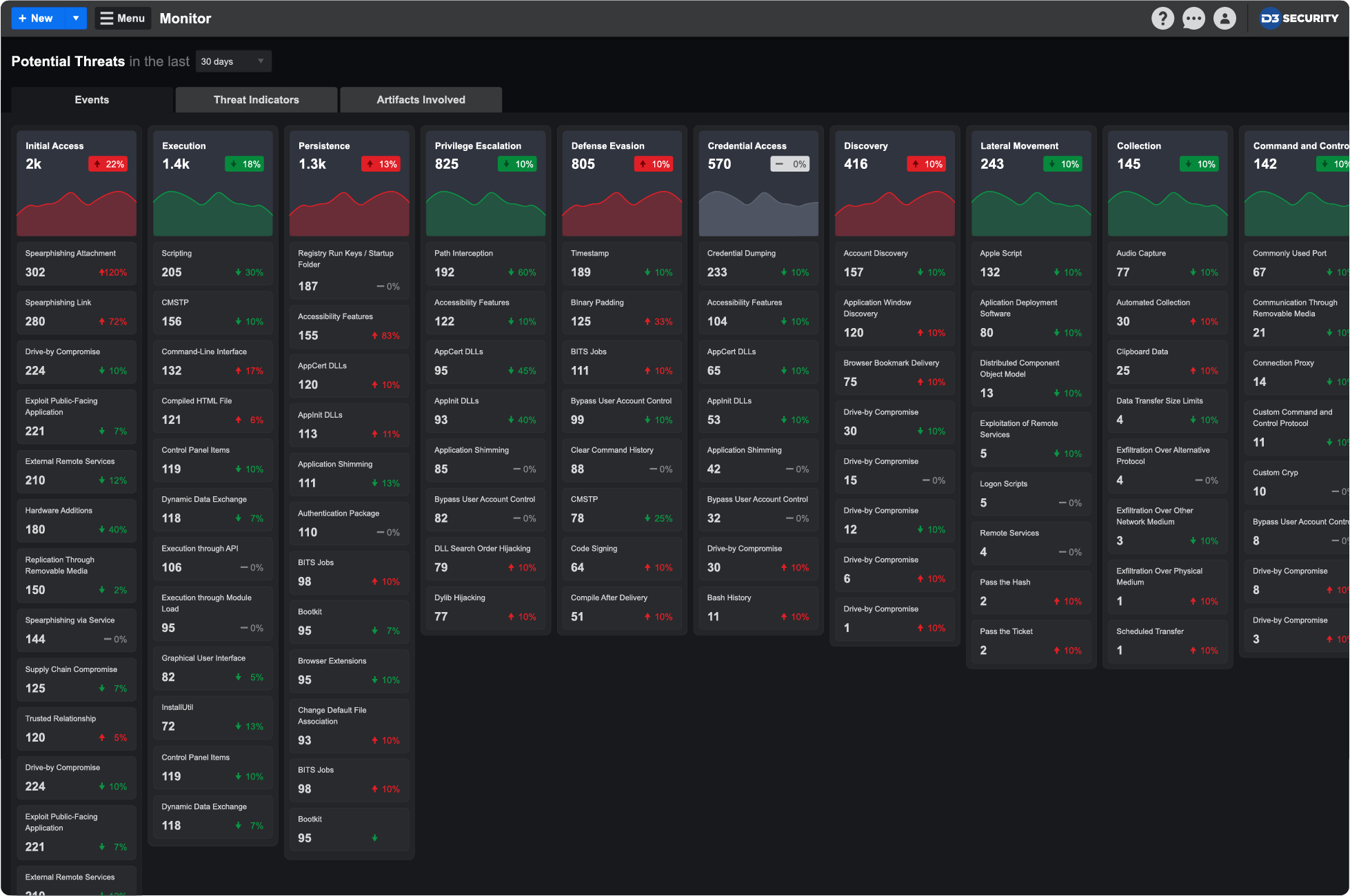
D3’s Monitor Dashboard places every incoming event into a visualization of the MITRE ATT&CK Matrix, showing the frequency with which every TTP has been detected in the environment. The different tabs of the dashboard also allow users to zero in on indicators, artifacts, and even the geolocation associated with each event.
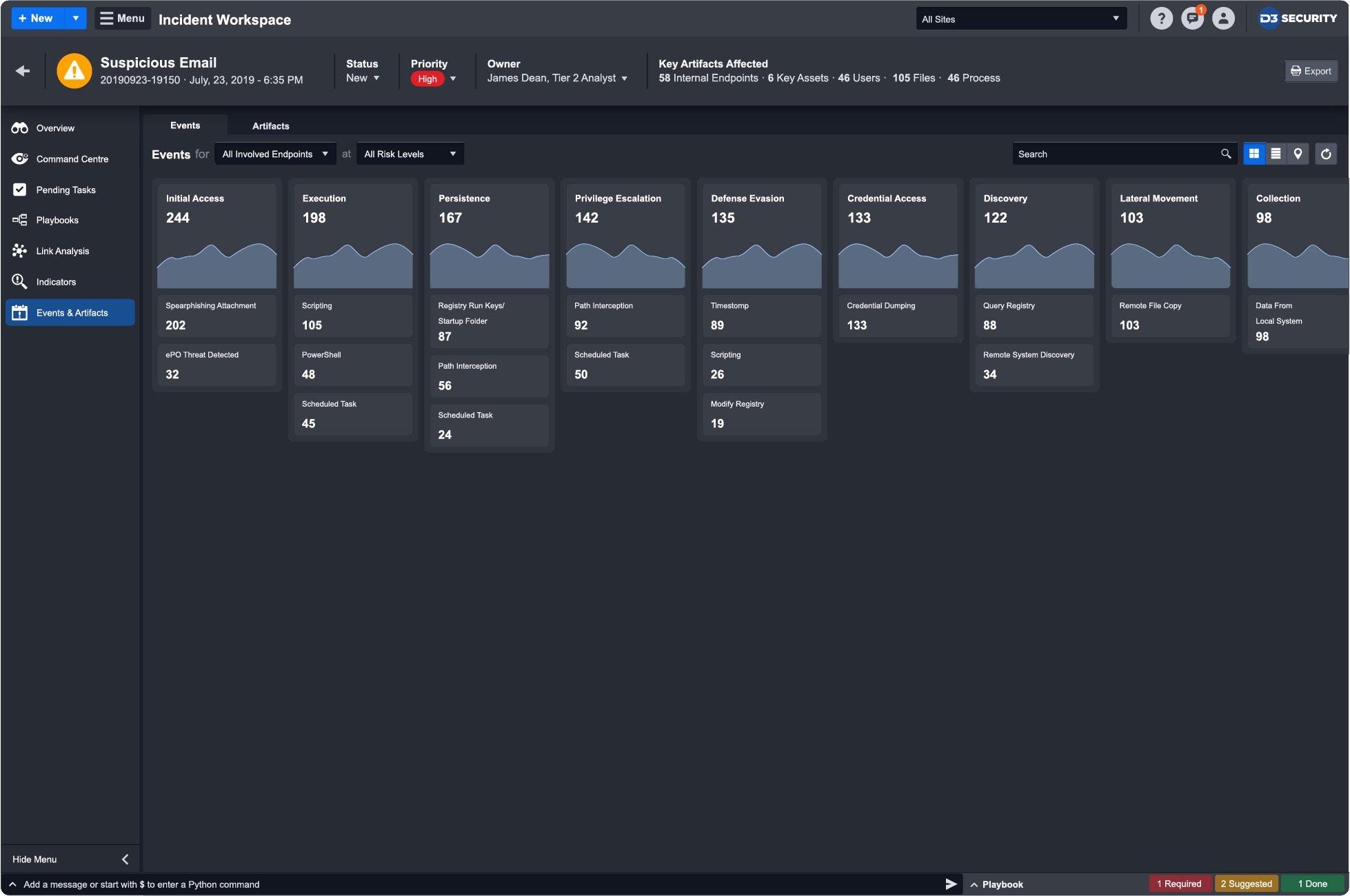
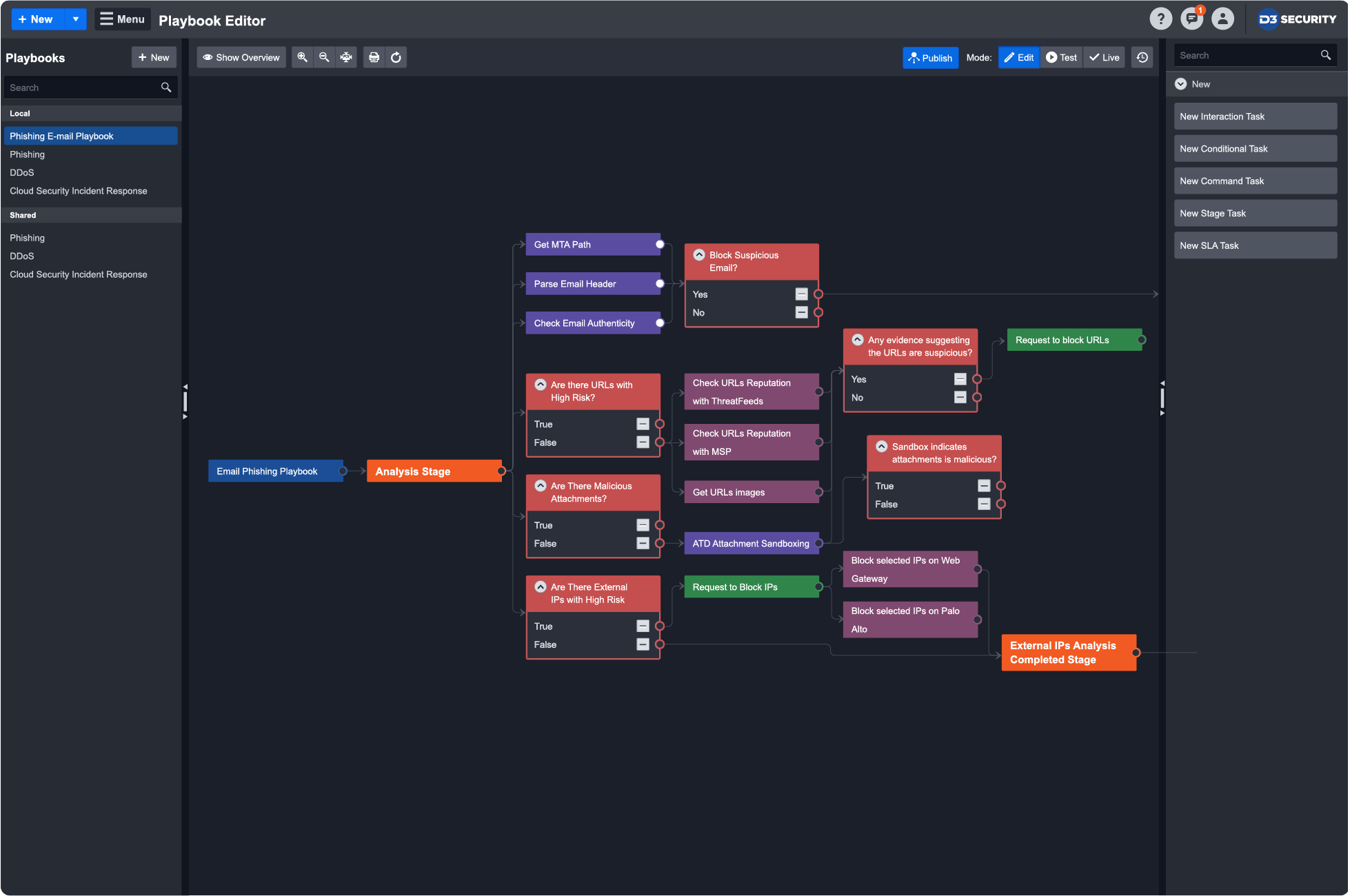
Based on the ATT&CK techniques detected in an alert, D3 can search across endpoints, network logs, email protection systems, SIEM logs, and more to find related IOCs and adversary techniques. This positions D3 as the ideal investigation hub for the next generation of complex cybersecurity attacks.
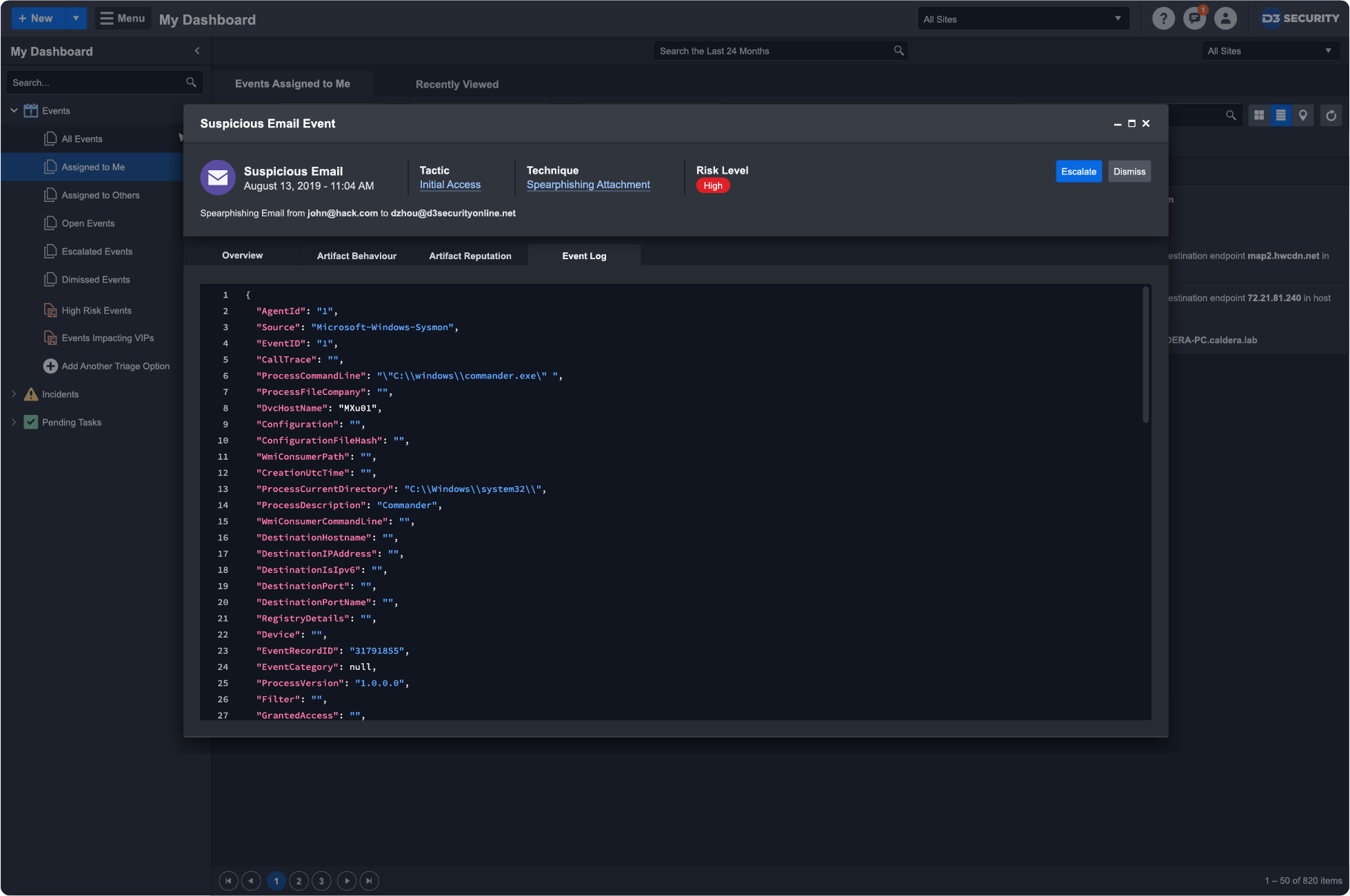
ATT&CK helps incident responders quickly validate threats, find related IOCs to uncover the extent of the attack, and trigger automation-powered playbooks to disrupt the kill chain. All the contextual data that D3 gathers informs the playbook that orchestrates response across 300+ integrated tools.
Because D3 aggregates events from across your entire security infrastructure it can generate comprehensive reports that show what techniques, tactics, and adversaries your SOC has faced. The report can break down which have succeeded and which have not—revealing gaps and issues that can be flagged for action.